The human domain is complex and unpredictable, and as a result the logic behind certain behaviors are also complex. The problem that many detection systems try to resolve is the automated detection of these complex behavior actions. Some of the actions are obvious (i.e. ports scan), but others are less detectable, particularly when is coming from the internal network such as valid credentials used for wrong purposes.
To make the issue a little more difficult, not all analysts use the same techniques or methods to achieve their goals. For example, a nation state actor could have a set of known techniques tactics and procedures (TTPs) that could potentially be detected. If the TTPs changed, what new course of actions would the analyst take? Or even more frustrating, what if an insider was operating in the grounds of a company policy to steal data? The detection line grows and might even be non-existent in the case of an insider leaking information until the damage is done.
Threat Modeling
One of the fastest and effective means to detect who the adversaries are, is via threat modeling. In the most rudimentary example, a simple survey polling the current IR team can bring a solid list of potential, or known adversaries. This tacit knowledge is powerful because it is the shared body of knowledge that has been learned over many years. Often it is the assumed knowledge, or information that did not make it into a formal document.
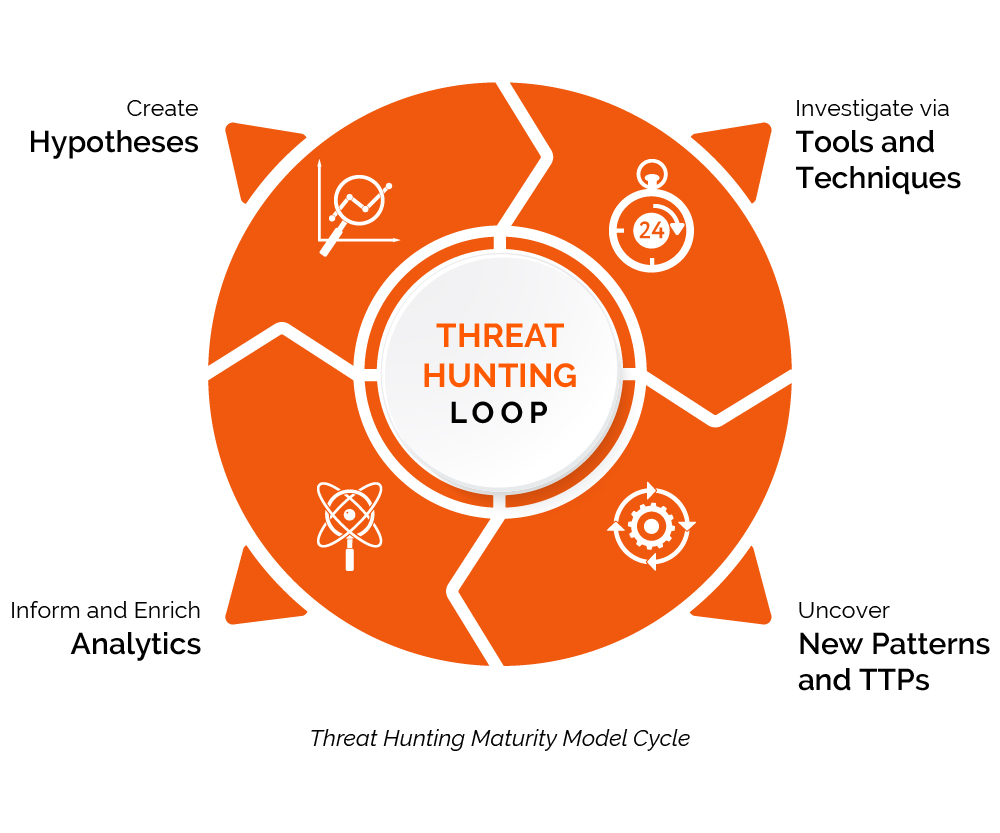
Introducing the Threat Hunting Maturity Model
This model is very similar to the Capabilities Maturity Model Integration (CMMI) which is a generic process model improvement.
Knowing what requires protection ensures the focus is on the most meaningful areas of the organization. Looking at who the adversaries are can also be extracted from the knowledge and reporting from the larger community. Based on these findings, the hunt priorities or intrusion analysis focus can be set forth. Geopolitical and other market factors help to further paint the adversary picture by helping to understand the actor’s motivation.
Threat Hunting
Threat hunting can be defined as the act of persistently capturing, tracing, and eradicating cyber adversaries as early as possible in the Cyber Kill Chain. The earlier you locate and track the adversary in the chain the less impacting activities he will carry on to the network. The organization IR team can benefit by obtaining better visibility and uncovering the organization’s weaknesses, early detection of threats, and damage control to name a few. Real Threat Hunting is the area that goes above any automated detection capabilities of an organization.
To recap; it is the point where the human analyst makes the decision call on whether or not there has been a compromise. Is also good to mention here that the more manual the detection area, the more skilled the Hunter task must be.
Not all hunts can produce indicators of compromise (IOCs), but when possible, it is the area where the human Hunter leverages automation and deep learning to assist with both behavioral and atomic types of detection. For the biggest return, hunting and incident response need to work together.
When possible, IOCs should be worked back into the automated detection system. Future alerts and detection patterns would trigger the IR process and not necessarily the Hunter. One such means to identify active adversaries is with the application of Active Defense, or Offensive Countermeasures.
To be continued….
This post is written by Carlos Vazquez, Sr. Cyber Security Consultant at DTS Solution

