Managed SOC / CSOC (aka Cyber Security Operations Center) is often regarded as the workplace where the nerdy information security professionals spend their time in. Actually, its more than just a physical workplace with many more dimensions to it. So, let’s see what makes a monitoring center with screens and eyes a SOC.
What is SOC
To an eagle’s eye, SOC is a facility where Information Security professionals monitor and analyze data and respond to threats to keep the organization safe from cyber-attacks. But this is just the tip of the iceberg. SOC consists of way more stuff. It includes a good security strategy, a fleet of security solutions strategically placed across the organization, a set of processes and procedures and some well-trained eyes to complement all that. All these combined the SOC is responsible for assessing and safe guarding the organization’s security posture.
HAWKEYE – CSOC As A Service powered by DTS Solution
Security Strategy:
Security Strategy is the back bone of the SOC and is considered most important in the security of the business. Developing a security strategy is where SOC starts and this is where most of the expertise are put in. SOC strategy varies greatly based on the line of business and threat vectors specific to the organization. The security strategy should be dynamic and elastic to cater ever advancing threats. All the other components of the SOC is to complement this. Frameworks like COBIT are used for security strategy development.
Each organization is different in many ways. Even the ones have the same line of business behave differently. So, strategy development starts with in-depth assessment of the organization itself, various security threats present and can show up in future and how to respond to them. The most important part of security strategy development is understanding each key element of the organization and plotting it. Elements would include the business itself, people, physical and logical assets. In this step elements are classified according to the value and risk. Then understand the threats and vulnerabilities that affect each element against the risks. This is where the security posture of the organization is understood. Now it’s time for a gap analysis and risk analysis to identify the missing links in security resources. The potential of each available resource is explored and once the detailed picture is drawn, brainstorm and get the hand dirty on the counter measures.
In a nutshell security strategy includes the outcome of all the points above how the SOC is deployed.
Processes and Procedures:
Security Processes and Procedures are the key guideline documents for how a SOC run without which security is an extreme chaos. For every step from security strategy to incident response, processes and procedures are defined. Processes include guidelines regarding how each threat scenario is handled. This has to be as elaborate as the people involved in a threat management, solutions to be used and step by step procedure to counter the incident.
Each process is evaluated and drilled at various levels to ensure the effectiveness. The process and procedures documents are standardized and shared across every stake holder in an organization’s security team.
Security Solutions:
So, now we have the high-resolution picture of the organization’s security posture which can be zoomed in to view the granular details of each element and everything documented. It’s time to engage the counter measures. Security solutions are top in the list of counter measures. For each kind of threats identified, risk analysis is performed and security solutions are deployed to tackle them. It can be anything from a security gate or surveillance camera to next generation firewalls. Solutions should be placed in a way that each asset or each bit of data passed though the organization’s network is carefully monitored.
An organization can have too many security solutions including but not limited to
- Firewalls to control the network traffic
- Endpoint monitoring solutions to protect the hosts
- DLP solutions to safeguard data
- Email protection systems
- Antivirus solutions
- Threat intel solutions
- Security gate and door access controllers
- And a plethora of network devices.
Monitoring all these separately will fatigue the security team. There comes to SIEM solution as the savior. Each of the network and security solutions will be generating logs and events for each activity. A SIEM solution can centrally monitor a warehouse full of this data and correlate it to identify threats and respond effectively. A well configured SIEM solution with a flavor of Artificial Intelligence can be considered as the most powerful weapon in the SOC arsenal.
And Finally, The SOC Monitoring Team:
If you ask me who is the SOC team, I would say: Everyone within the organization. In fact, a good SOC architecture has each employee of the organization working for it. Everyone within the organization has a lot to contribute to the security. A well matured SOC has each person trained on security processes and procedures specific to the organization.
When it comes to the SOC monitoring team. They are the team of well-trained security professionals who drives the SOC. To reiterate, they are just part of the SOC and NOT all of it. The team coordinates the security strategy and all the security processes and solutions defined to keep the security state of the organization high. They are the first ones to monitor, analyze and respond to each incident that arise. SOC monitoring team is distributed in different levels with assigned tasks based on severity and complexity. A Level-1 SOC analyst monitors the incidents and respond to it based on the process while complex incidents are escalated to a more experienced level of engineers. A SOC Manager coordinates all the processes to run the SOC architecture smoothly
While the SOC team doesn’t have to analyze each bit of data passes through the organization network by themselves, the team must be able set measures to identify each bit of undesirable traffic enters the network and respond to it. SOC monitoring is not a clerical job which includes analyzing each packet of data in a defined way. Rather they should be wizards who are always up to date with the new trends or cyber-attacks and are well prepared in counteracting them with the tools available quickly before the threat has any impact on the assets.
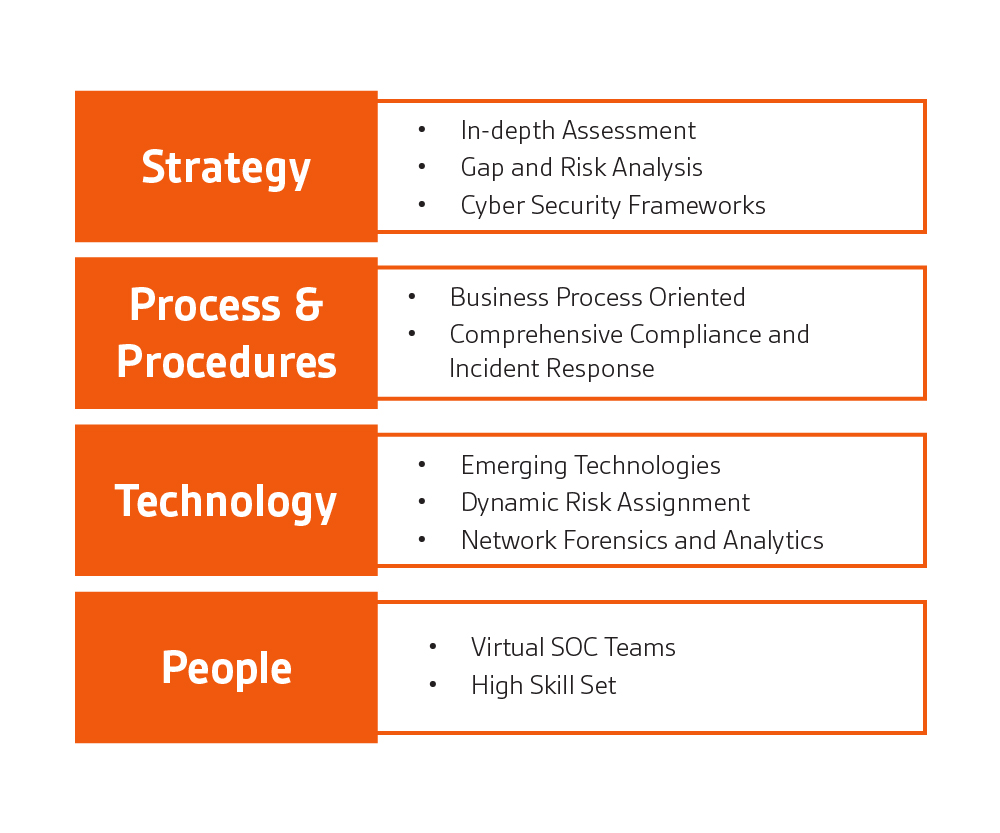
Components of a Cyber Security Operations Center
So, we have the SOC setup and what’s next?…
We can’t wait till the real attack to pitch in to assess the effectiveness of our SOC system. So, let’s begin the Cyber War Game…
Red-Blue Teaming
SOC professionals are generally categorized as two teams, the RED and BLUE teams. Red Team members are hard core hackers who put themselves in to the shoes of a real attacker and brutally attack the organization from inside and outside the network (obviously, in a controlled manner without bringing down the business). They try to sneak in to the physical and logical network assets of the organization by simulating real world attacks to find out the loop holes in our security shield. Red team can use various techniques like Phishing, Firewall Intrusion, Vulnerability Exploitation or DOS attacks to break in to the network. The results of each attack are documented to be fixed.
Meanwhile Blue Team is the guardians of the network. When Red team performs the attacks, Blue team defends it by monitoring the network, detecting the type of attacks, fixing vulnerabilities and by addressing the recommendations of the RED team. It’s Blue team’s job to constantly monitor the assets and keep it away from the hands of a potential attacker. Blue Team uses a plethora of techniques for this like, constantly monitoring the network traffic, configuring all the network/security devices as per security standards, user access management, vulnerability identification and patching, etc.
Threat Hunting:
Read here: The Basics of Threat Hunting
As it sounds, Threat hunting simply means various techniques for hunting for threats in the network. Threat hunting can be performed in different ways:
Log/Traffic analysis: This is the traditional and manual process of inspecting logs and traffic packets by trained security analysts to identify threats by analyzing patterns. It is generally slow and not very effective as the human factor limits only identifying the known patterns.
Intelligent SIEM Solutions: Advanced SIEM Solution uses correlation rules and machine learning techniques to identify threats. Correlation rules are often configured to identify threat signatures or patterns from logs and network traffic monitoring data. While machine learning techniques uses techniques like Clustering, Regression and Classification to find out anomalies in the data stream. Once threats are identified, either they are alerted to Blue Team to respond or automatically responded by the SOAR solutions. Most of the advanced SIEMs are equipped with a SOAR capability in built.
Threat Intelligence Feeds: Threat intelligent feeds are repositories of Threat data. It can have lists of malicious IP address, domains, file signatures, email addresses, etc. Smart Security solutions like SIEM and Advanced Firewalls use this database to match the network data presented and identify threat actors.
Threat Advisory Simulation:
So, now we know how to identify threats. Is the SOC equipped to respond to each incident? Threat Advisory Simulation techniques simulate attacks within the network just as in real-world assuming that it’s a real attack and see how the security team respond to it just like in a fire drill. Each step of Incident Response from Threat Identification to Containment are put to test here. Gaps are identified and fixed.
So, we have our SIEM setup and tested. Are we done? Well, a big NO. In cybersecurity, what’s tomorrow is not what’s today. Attacks ever evolving and new threats are emerged every day if not every hour. So, all the processes listed above are cycled back and back at decided interval to keep the business up and running.
To conclude, it’s just a well spread myth that the SOC is a well-lit room with many screens and security professionals looking at it. This belief could be the primary reason why even some of the well invested CSOCs fail. This is where experienced SOC professionals like HAWKEYE can help. With years of expertise in end-to-end SOC development, professionals will be able to walk you through the complex path of SOC development like a cake walk.
This post is written by Ranjith Kesavan, Sr. Cyber Security Lead – Operations Center (SOC and Blue Team) at DTS Solution

