We are living in a world where any number of cyber threats can bring an organization to its knees and it can be downright terrifying. Few years ago, threat intelligence first became a new buzzword in cybersecurity. Threat intelligence was not always a concept easily understood by typical IT security professionals.
Intelligence can be derived from lists/files which contains the information about IP’s, hashes and URL’s, but that information and the objects in the lists themselves are not intelligence. Threat Intelligence is taking available data and extracting meaningful information from that data related with the threat actor’s action for the purpose of providing insight into decision-making.
The main purpose of threat intelligence is to help organizations and understand the risks of the most common and severe external threats, such as advanced persistent threats (APTs), zero-day threats, and exploits. After all, threats require appropriate defense, and cyber threat intelligence delivers the capability to defend more proactively. It provides context — like who is attacking you, what their motivation and capabilities are, and what are the Indicators of Compromise (IoC) in your systems to look for — that helps to make informed decisions about your security.
Importance of Threat Intelligence in Cyber Security
Any business that stores and works with the data related with financial or personal that might be valuable to hackers — should consider cyber threat intelligence as an element of its cyber security plan. Threat intelligence supports various organizations by providing them vision into the mechanisms and indications of threats, allowing them to build defense strategies and frameworks, and reduce the attack surface which results protection of the network.
Security operations, incident response, fraud prevention, vulnerability management, risk management, security planning and decision-making all the areas benefit from the context that threat intelligence provides. Some organizations try to incorporate threat data feeds into their network, but they are not sure about what to do with the extra data, adding to the burden of analysts who may not have the right tools to decide what to prioritize and what to ignore. In this scenario, the role of Threat Intelligence comes into play. It prioritizes removing false positives and recognizing the advanced threats and exploits, the organization is most vulnerable to, so that the SOC teams can take action against them. A wide knowledge of what’s happening outside our network are provided by Threat Intelligence to organizations, giving them better visibility of the cyber threats which bring the most risk to their infrastructure.
The best threat intelligence solutions integrate with the existing solutions and use machine learning to automate data collection and processing unstructured data from disparate sources, and then connect the dots by providing indicators of compromise (IoCs) and the tactics, techniques, and procedures (TTPs) of threat actors.
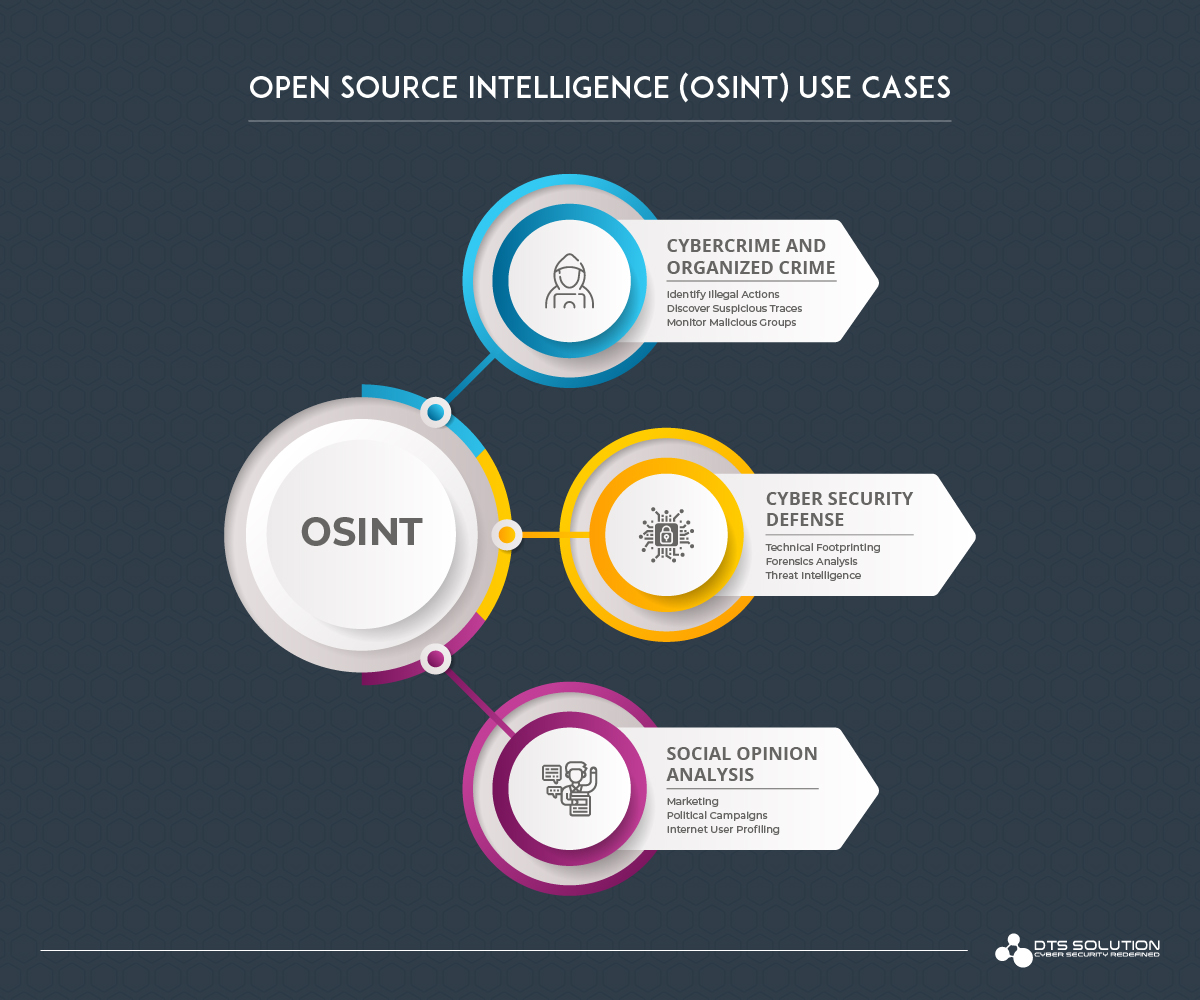
Open Source Intelligence (OSINT)
Open Source Intelligence are information or data which are accessed and gathered from public sources for any specific purpose. The most common OSINT is known to be Internet where it includes blogs, social media, websites, government portals, deep web and sometimes even the dark web. OSINT also includes traditional channels such as Newspaper, Television, Radio, Magazines; Books, Academic Publications such as journals & research papers etc.
OSINT can be used by the public civilian for basic knowledge, business, and public opinions; by government for any national threat analysis, services; by any cybercrime groups for any illegal activities; and by a cybersecurity professional for technical foot printing, cyber defense.
OSINT in relation with Cyber Security Threat Intelligence
As mentioned earlier, OSINT can be used by any cyber criminals for any illegal activity. These threat actors use OSINT mainly for the purpose of monitoring and researching their victims. This practice of researching and gathering information about a person or entity for any malicious intent is known as doxing. The cyber stalkers use this readily available information to examine their target’s business, products, weaknesses which then can be exploited for any activity they desire. The proper way to protect from these kind of threats is to be vigilant and careful in what information are being shared online.
Now for someone like a SOC analyst, OSINT can be used in researching oncoming threats and data. The collected information will help the analysts in making decisions on whether to dismiss the event or to perform appropriate action, if the event is a valid threat. Identifying the most useful tools and techniques will be much more achievable.
The required action can include further research of an IP address and file binary, restricting incoming traffic from a blacklist IP address, Software patching, detect any sensitive information leaks etc.
OSINT Implications to Cybersecurity:
1. Ethical Hacking and Penetration Testing
Security professionals utilize open source intelligence (OSINT) to discover potential weaknesses in the organization’s networks, so that they can be remediated before they are exploited by threat actors. The first phase of any penetration testing methodology begins with reconnaissance (in other words, with OSINT). Commonly found vulnerabilities include: Open ports or unsecured internet-connected devices, unpatched software, Accidental leakage of sensitive information on social media sites, Open ports or unsecured internet-connected devices, unpatched software etc.
2. Recognizing External Threats
OSINT identifies external threats from various sources for e.g., the internet is an excellent source of insights into an organization’s most advanced threats. Open Source Intelligence enables IT security professionals to prioritize their time and resources to address the most significant threats in order to prevent and mitigate data breaches, thwart cyber-attacks and also to identify the new vulnerabilities which are being actively exploited.
Security analysts in SOC can leverage the benefits of OSINT and tackle the issues faced to normalize and optimize the Cyber Threat Intelligence (CTI) operations. The CTI platforms enable the creation of detailed threat analysis by working together among peer organizations by sharing relevant, structured and enriched threat information.
The most important factor in the success of any open source intelligence initiative is the presence of a clear strategy, understand the target and set the objectives to accomplish the goal accordingly.
This post is written by Nithu Thankam Johnson, Cyber Security Analyst at DTS Solution

