In this blog post, we will explore the details of Citrix ADC vulnerability, its potential consequences, and the importance of responsible vulnerability management.
Understanding CVE-2023-3519
CVE-2023-3519 is a security flaw that affects Citrix ADC Gateway, a widely used application delivery controller and load balancer. It allows attackers to remotely execute arbitrary code on vulnerable systems. The vulnerability is categorized as a stack overflow, wherein the attacker can overwhelm a specific memory buffer, causing it to overwrite adjacent memory areas and execute malicious code.
The alarming aspect of this vulnerability is its simplicity, as it does not require authentication to exploit. Furthermore, the lack of certain exploit mitigations, such as PIE (Position Independent Executable) and stack canaries, makes it easier for attackers to exploit the vulnerable function on certain versions of the software.
According to the report, approximately 61,000 Citrix ADC appliances are exposed to the internet, and an alarming 53% of them remain unpatched. This means that over 32,000 devices are still susceptible to potential exploitation.
Vulnerable Devices in UAE
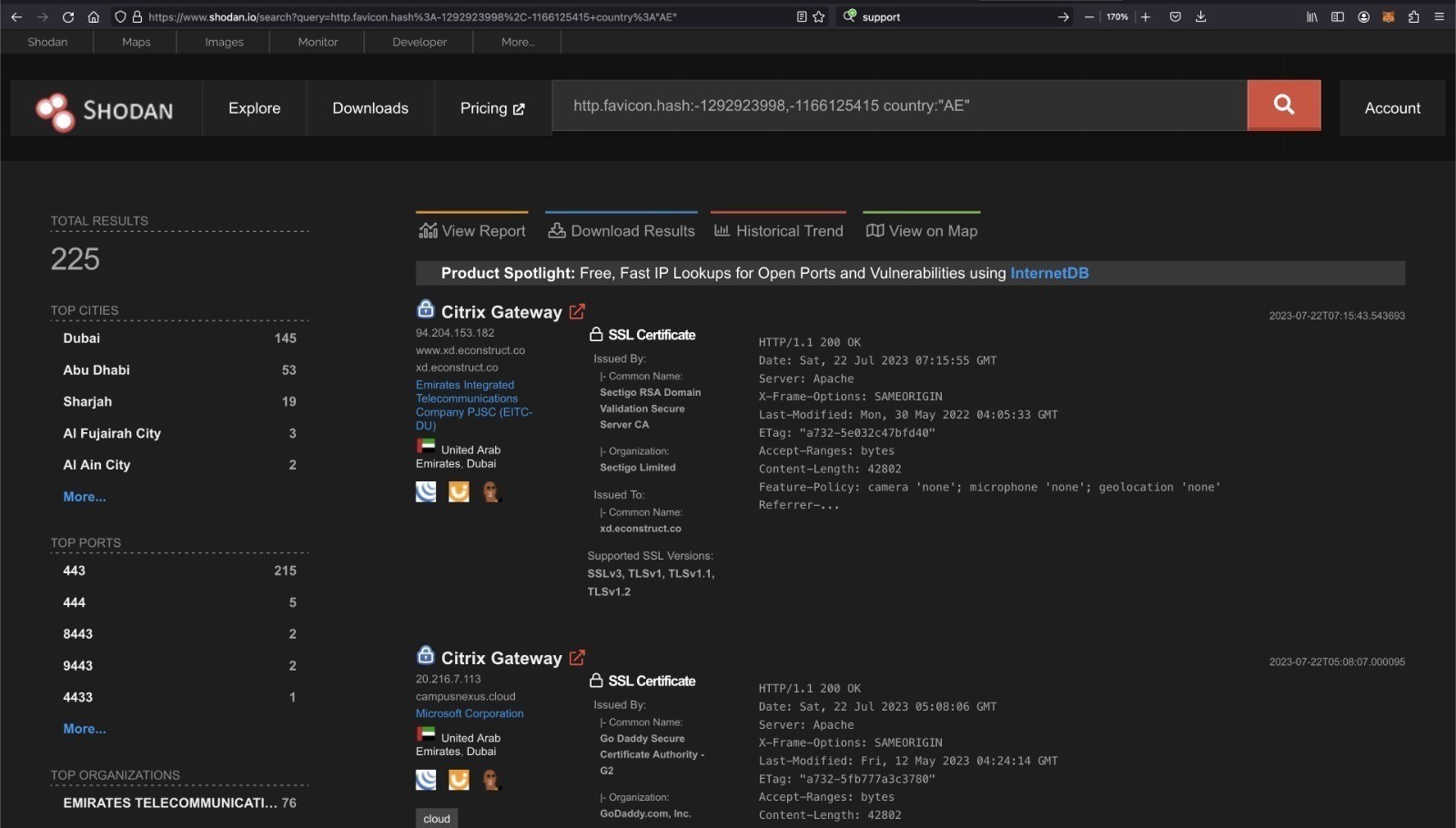
HawkEye Labs security team did some research and could see multiple devices that are vulnerable in UAE. Here is a screenshot that has a total of 225 devices which are vulnerable to this at the time of writing this blog post.
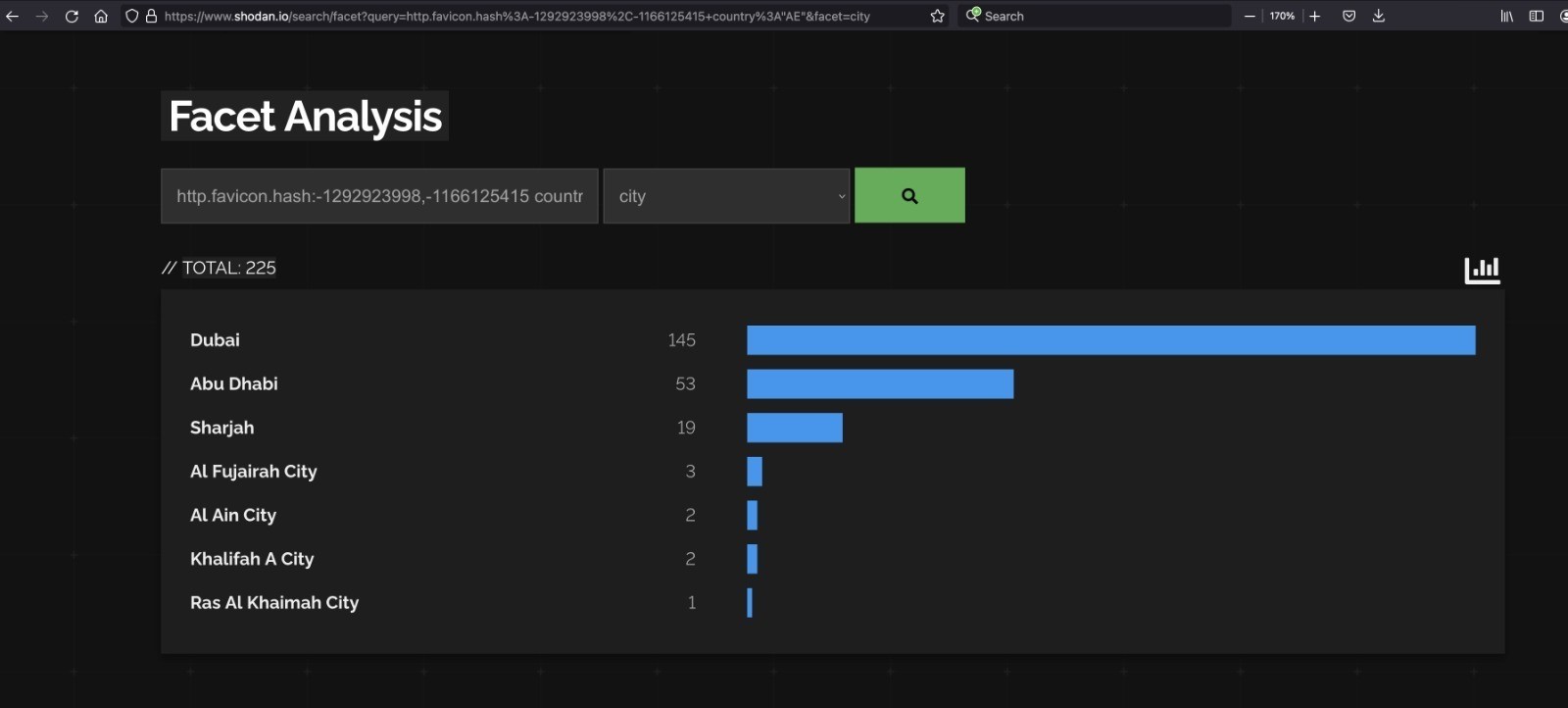
From the above, Abu Dhabi has the greatest number of vulnerable devices followed by Dubai. Here is a screenshot with the city-wise break down:
Here is the Shodan search string that you could use and check if you are exposed.
http.favicon.hash:-1292923998,-1166125415 country:”AE”
http.favicon.hash:-1292923998,-1166125415
Below are the recently disclosed vulnerabilities seen been used in the wild:
CVE-2023-3466:
Affected Products: Citrix ADC, Citrix Gateway
Description: Reflected Cross-Site Scripting (XSS)
Requirements for Vulnerability Exploitation:
Requires the victim to access an attacker-controlled link in the browser while being on a network with connectivity to the NSIP
CVE-2023-3467:
Affected Products: Citrix ADC, Citrix Gateway
Description: Privilege Escalation to root administrator (nsroot)
Requirements for Vulnerability Exploitation:
Authenticated access to NSIP or SNIP with management interface access
CVE-2023-3519:
Affected Products: Citrix ADC, Citrix Gateway
Description: Unauthenticated remote code execution
Requirements for Vulnerability Exploitation:
Appliance must be configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) OR AAA virtual server
The affected versions of Citrix Products are as follows:
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.13
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-91.13
- NetScaler ADC 13.1-FIPS before 13.1-37.159
- NetScaler ADC 12.1-FIPS before 12.1-55.297
- NetScaler ADC 12.1-NDcPP before 12.1-55.297
Patch/Fix:
Citrix has released patches for this vulnerability. Below is the fix versions:
- NetScaler ADC and NetScaler Gateway 13.1-49.13 and later releases
- NetScaler ADC and NetScaler Gateway 13.0-91.13 and later releases of 13.0
- NetScaler ADC 13.1-FIPS 13.1-37.159 and later releases of 13.1-FIPS
- NetScaler ADC 12.1-FIPS 12.1-55.297 and later releases of 12.1-FIPS
- NetScaler ADC 12.1-NDcPP 12.1-55.297 and later releases of 12.1-NDcPP
How to verify that you are patched:
There are few exploit checks that you could use. For example, you could run the below opensource tool to check if you are vulnerable.
git clone https://github.com/telekom-security/cve-2023-3519-citrix-scanner
cd cve-2023-3519-citrix-scanner
echo “test.com” >> targets.txt
python3 CVE-2023-3519-checker.py
If the output contains string “patched: True”, then it does indicate that the issue is fixed.
Alternatively, you could use a scanner such as Tenable to perform a scan.
Source/References:
https://www.tenable.com/blog/cve-2023-3519-critical-rce-in-netscaler-adc-citrix-adc-and-netscaler-gateway-citrix-gateway
https://github.com/telekom-security/cve-2023-3519-citrix-scanner