The phishing technique known as QR code phishing, sometimes known as quishing, employs QR codes to entice victims into exposing private information. Threat actors generate QR codes that appear to be genuine—for example, ones that claim to give a discount or special offer—but in reality take the victim to a fraudulent website under the attacker’s control.
Background:
Before an attack can be transmitted to the target (often via email), the QR code itself is required. A cybercriminal may now design a QR code and link it to a phishing website quite easily. The QR code is then included in a phishing email that instructs the recipient to scan it in order to access certain information. A typical strategy, for instance, is to allow individuals to use a QR code to access an encrypted audio message. The victim then accesses the QR code with their camera, launches their browser, and is sent to a phishing website.
According to reports, Quishing attacks had grown since the beginning of the COVID-19 epidemic, when an increasing number of trustworthy businesses began utilizing QR codes to facilitate low-contact transactions. Instead of giving guests physical copies of their menus, some eateries, for instance, link QR codes to online versions. QR codes are used by digital wallets to enable contactless payments. Quishing prospects have grown as consumers have become accustomed to engaging with QR codes daily.
QRLJacking Attack
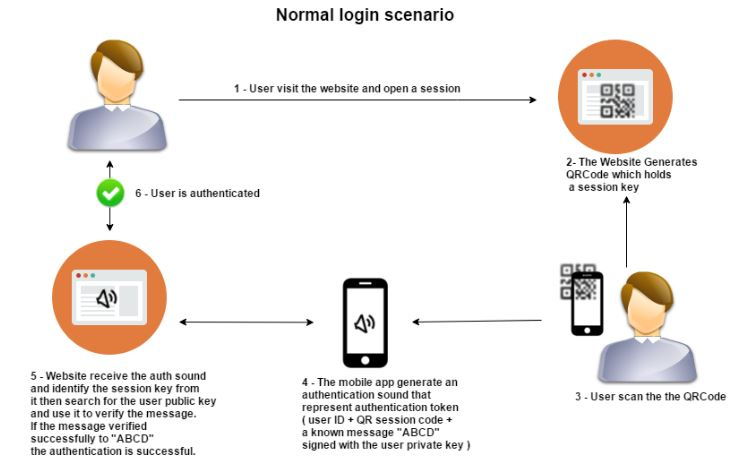
The Quick Response Code Login (QRL) system verifies users by scanning QR codes. Instead of typing in usernames and passwords, users may log in by just scanning the QR codes that are presented on the online apps. Here are some quick steps:
- The user visits the website and requests login.
- For the session, the web application creates a special QR code. The code could include a server URL, a token, and an expiration date.
- The user scans the QR code shown on the web application using the QR code scanner in the relevant mobile app.
- The mobile application sends the web application the token and credential information.
- The web application verifies the token and confirms the user’s identity.
QRL Scenario (Source: OWASP)
Attacks against QRL are known as “Quick Response Code Login Jacking (QRLJacking)”. In place of the service provider, the user scans the attacker’s given QR code, giving the attacker access to the user account.
QRLJacking Attack Scenario (Source: OWASP)
EvilQR Kit
Evil QR is a variation of a QRLJacking attack that shows how hackers may hijack accounts by tricking users into scanning provided QR codes using phishing. This tool is developed by Kuba Gretzky and can be found on https://github.com/kgretzky/evilqr.
Working:
- The attacker opens the official login page within their web browser to generate the sign-in QR code.
- Using the Evil QR browser extension, the attacker is able to extract the sign-in QR code from the login page and upload it to the Evil QR server, where the phishing page is hosted.
- The phishing page, hosted by the attacker, dynamically displays the most recent sign-in QR code controlled by the attacker.
- Once the victim successfully scans the QR code, the attacker takes control of the compromised account.
Every website may have a unique phishing pre-text with dynamic changes to customize the Evil QR attack. Regardless of how a website is presented, the Evil QR browser extension will be able to find and extract QR codes within it. The extension allows for the extraction of QR codes displayed as CANVAS, IMG, SVG, or even DIV (by using the html2canvas library to take a screenshot).
Working of Evil QR
The server was created in GO, and its major functions are to operate an HTTP server to host the phishing website and provide REST API for the browser extension. It is awaiting authorized communication from the browser extension that includes a JSON-formatted picture of a QR code.
{
“id”: “11111111-1111-1111-1111-111111111111”,
“source”: “data:image/png;base64,iVBORw0K…”,
“host”: “discord.com”
}
After that, the obtained QR code is saved and made accessible to the JavaScript running on the phishing page for retrieval. Instead of utilizing Websockets, the phishing page uses HTTP Long Polling to quickly obtain updates for QR codes.
Detection and Prevention
- Verify the URL after scanning a QR code to make sure it leads to the intended website and looks legitimate.
- while logging into a website through a QR code, use caution while inputting any personal, financial, or login information.
- To complete a transaction, avoid paying using a website that may be reached via a QR code and instead manually type a recognized and reliable URL.
- Be wary of unusual and urgent requests, particularly if they come with threats.
- Instead of downloading an app straight from a QR code, look for it in the app store on your phone.
- Add a secure QR scanner to your system. Before you access a scanned link, certain antivirus providers’ QR scanner apps verify its security. They are capable of spotting risky sites, forced software downloads, and scams.