We have been subjected to fraudulent emails from the early days of the internet, from intrusive spam to highly targeted and customized phishing efforts. Bad actors will always manage to keep one step ahead, coming up with new ways to bypass filtering laws and other regulations aimed to clean up our inboxes, despite substantial breakthroughs in email detection and blocking over the years.
Background
A sophisticated email phishing operation that took use of genuine Salesforce email services and SMTP servers’ 0-day vulnerability has been discovered by Guardio’s Email Protection. The research team at Guardio Labs has discovered an actively exploited vulnerability that allows threat actors to create customized phishing emails using the Salesforce infrastructure and domain. It uses an obsolete tactic: sending malicious emails while concealing them behind typically trusted mail gateways so that the emails won’t be blocked by defense mechanisms.
Phishforce Vulnerability
Customers of the Salesforce CRM are able to send emails under their own brands utilizing verified custom domains. This prevents users from impersonating other brands in emails they send using Salesforce without authorization.
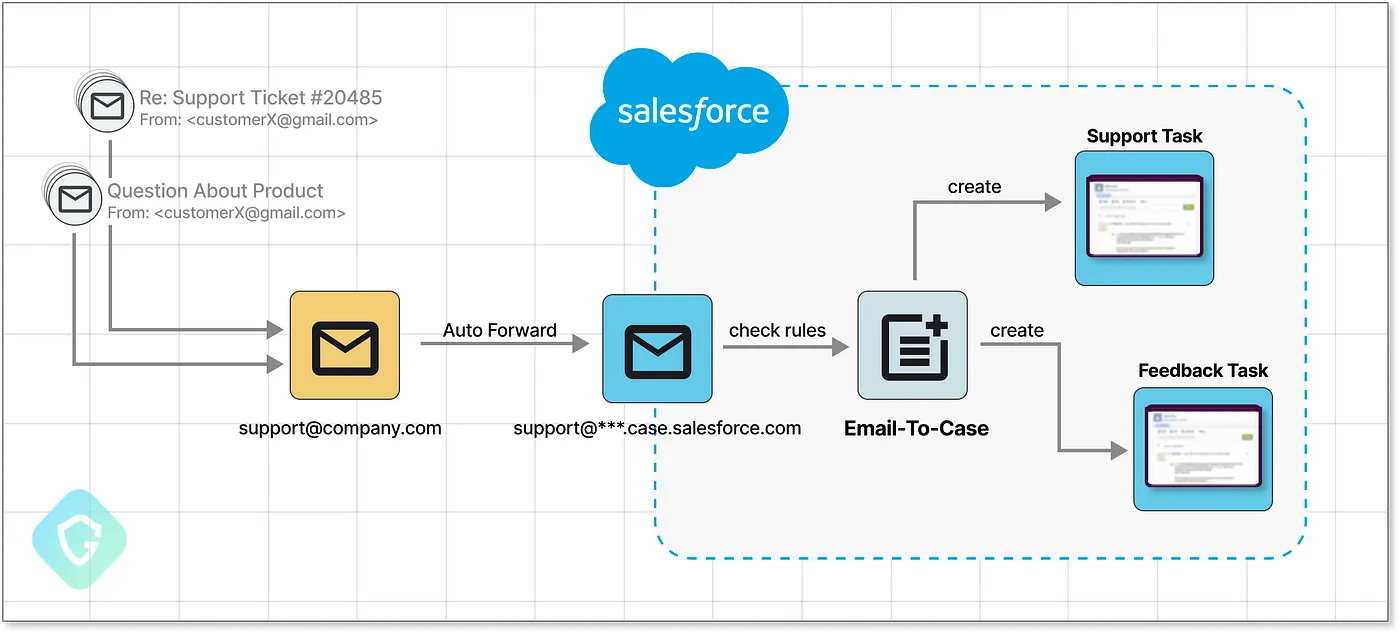
Guardio Labs, however, reports that the attackers discovered a way to take advantage of Salesforce’s “Email-to-Case” tool, which businesses employ to turn incoming client emails into usable cases for their support staff.
A common “Email-To-Case” Flow in Salesforce Eco-System (Guardio)
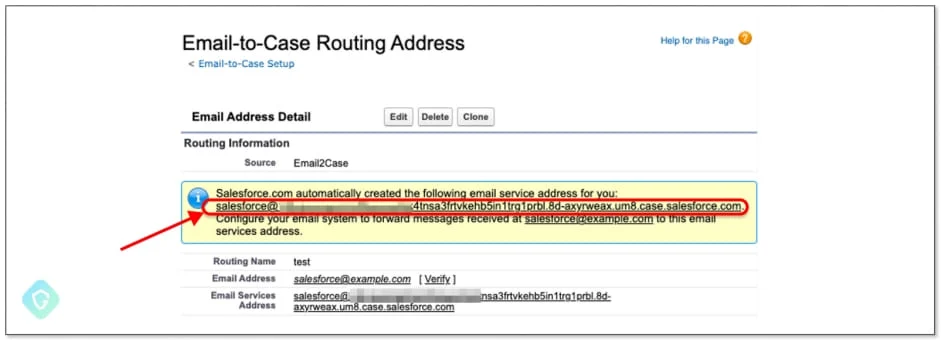
In order to take control of a Salesforce-generated email account, the attackers specifically set up a new “Email-to-Case” flow and then made a new inbound email address on the “salesforce.com” domain.
Generated Salesforce address (Guardio Labs)
After that, they configured the address as an “Organization-Wide Email Address,” which Salesforce’s Mass Mailer Gateway utilizes for outgoing emails, and lastly, they went through the verification procedure to validate ownership of the domain. Through this method, they were able to send emails to anybody using their Salesforce email address, getting through both Salesforce’s verification safeguards and any other email filters and anti-phishing measures in place.
The phishing kit used in this attack includes ways to go around two-factor authentication in order to acquire Facebook account credentials.
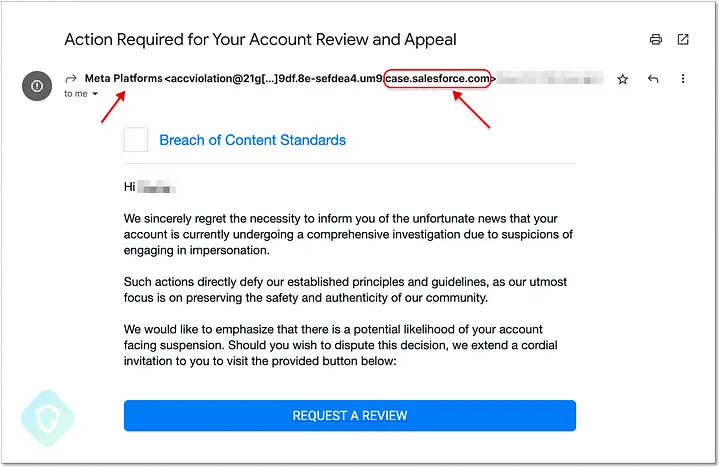
The message’s circled portion displays the “@salesforce.com” domain, yet it is identified as originating from “Meta Platforms.” That ought to serve as a red flag that this email is a phishing scam. Another error is the label on the large blue button, which reads “Request a Review.” It doesn’t: When a user clicks on this button, a phishing website designed to steal their Facebook account information is delivered in its place.
The phishing page is hosted by Facebook and appears to be some type of game, which is the second red flag. However, the page also contains stuff unrelated to gaming. The ingenious aspect of this comes into play here: Using Salesforce.com’s official email gateway services, the malicious email is sent from a salesforce.com email address and contains a genuine link to facebook.com. Essentially, this appearance of respectability is a cover for the malicious email.
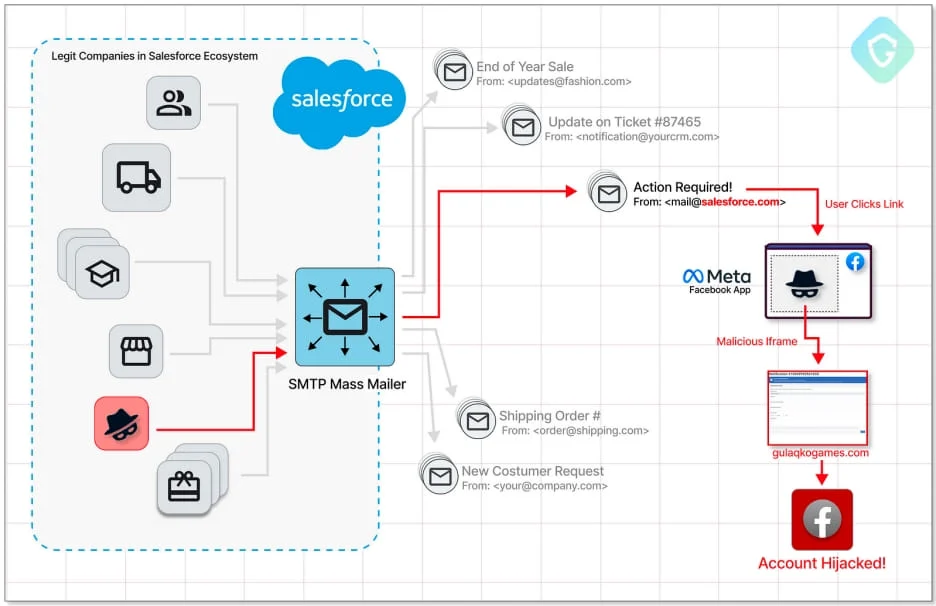
Attack Chain
Attack Chain – Guardio Labs
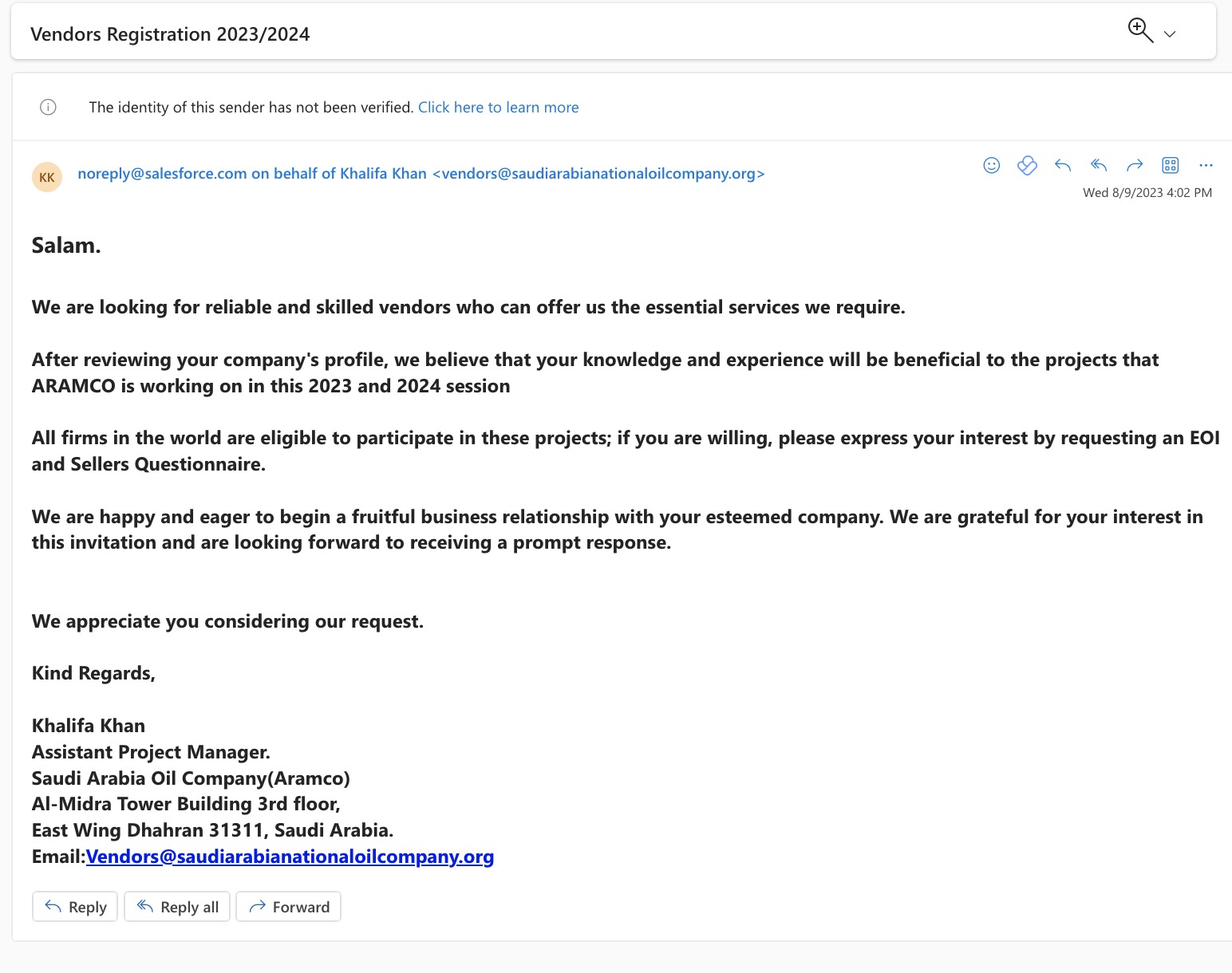
Recently we received a suspicious email from “noreply@salesforece.com” regarding vendor registration abusing the same phishforce vulnerability. On first look, it is a bit difficult to classify it as a phishing email as it is received from a trusted sender bypassing anti-phishing mechanisms.
IOCs
https://apps[.]facebook[.]com/360554927295924
https://gulaqkogames[.]com
fb-003applyonlines[.]web[.]app
facebook[.]com/104350419408426
facebook[.]com/124762450675931
qkemiskkd[.]top
aslpls[.]io
lucafaioni[.]com
g5e[.]tech
carlogamesaqol[.]com
panthergrandpa[.]com
metaoperations-inc[.]com
operations-ntfaccounts[.]com
page-account-restricted68540.firebaseapp.com
meta-business-appeal82[.]web[.]app
meta-business-appeal89[.]web[.]app
meta-business-appeal46[.]web[.]app
meta-business-appeal35[.]web[.]app
meta-business-appeal22[.]web[.]app
page-account-restricted68540[.]web[.]app/
case-report-1883849[.]com
pagerestricted-request-658021[.]web[.]app
pagerestricted-requestreview[.]web[.]app
meta-appeal-dashboard-5206-648[.]web[.]app
meta-appeal-dashboard-15689172[.]web[.]app
meta-appeal-request-1322951185[.]web[.]app
meta-business-appeal89[.]web[.]app
meta-business-security-6101621[.]web[.]app
meta-business-security-68420[.]web[.]app
meta-business-helpcenter-11694[.]web[.]app
metabusiness-109309686880[.]web[.]app
metabusiness-109309081074[.]web[.]app
metabusiness-10930909301[.]web[.]app
metabusiness-109680932[.]web[.]app
metabusiness-case189719825[.]web[.]app
meta-marketing-violation-57093[.]web[.]app
meta-appeal-review175980171[.]firebaseapp[.]com
meta-appeal-case151827296[.]web[.]app
meta-appeal-case167985122[.]web[.]app
meta-appeal-business-59049[.]web[.]app
meta-complain-copyright[.]com
business-request-review127989[.]web[.]app
Business-account-15781759289[.]web[.]app
Enhancing Cybersecurity: Collaborative Strategies Against Phishing and Scams
Continued vigilance is crucial as the landscape of cyber threats continually shifts and adapts. As attackers refine their tactics, it’s essential for organizations to adopt a multi-layered defense approach. Alongside technical solutions, user education plays a pivotal role in the fight against phishing and scams. Empowering users to recognize suspicious emails, URLs, and attachments can significantly reduce the success rate of such attacks.
Moreover, collaboration between email service providers, security firms, and law enforcement agencies is paramount. Sharing threat intelligence and staying updated on emerging attack vectors can lead to quicker detection and mitigation of threats. Additionally, fostering a culture of reporting among users can aid in tracking and dismantling phishing campaigns.
In the long term, advancements in artificial intelligence and machine learning hold promise for more sophisticated threat detection. These technologies can analyze patterns, anomalies, and behavioral indicators to flag potentially malicious activities. As phishing attacks become more personalized and targeted, AI-driven solutions could provide an edge in identifying and neutralizing these threats effectively.
Ultimately, the battle against phishing and scams is an ongoing effort that demands a united front from both technology providers and end-users. By continuously adapting strategies, refining security measures, and staying informed about emerging threats, the industry can work together to create a safer digital environment.