Using a mix of outdated and modern techniques, the Cuba ransomware group has been seen launching attacks against American critical infrastructure organizations and Latin American IT companies.
Background
Early in June 2023, the most current campaign was identified; as of this writing, CVE-2023-27532 is being used by Cuba to steal credentials from configuration files, according to BlackBerry’s Threat Research and Intelligence team.
The specific vulnerability affects Veeam Backup and Replication (VBR) products, and an exploit has been available since March 2023. The use of CVE-2023-27532 by FIN7, an organization with several documented links to different ransomware operations, was previously made public by WithSecure.
Cuba Ransomware Group
In the years since it first debuted on the threat landscape in 2019, Cuba ransomware, also known as COLDDRAW ransomware, has built up a relatively small but carefully chosen list of victims. Due to a distinctive marker that is included at the start of all encrypted files, it is also known as Fidel ransomware. This file marker serves as a reminder that the file has been encrypted to the ransomware and its decoder.
Cuba employs the double-extortion strategy, like many other ransomware authors, to “encourage” victims to make a payment. Cuba has employed a consistent set of core TTPs for the past four years, with minor variations from year to year. These often include commercial and customized malware, vulnerabilities, LOLBins, and well-known reliable pen-testing frameworks like Cobalt Strike and Metasploit.
CVE-2023-27532 (Veeam)
This vulnerability affects the legitimate Veeam Backup & Replication software, allowing an attacker to potentially gain access to the credentials stored within the configuration file on the victim’s device. It is exploitable via the Veeam backup service, which runs on the default TCP port of 9401.
The exploit works by accessing an exposed API on a component of the Veeam application — Veeam.Backup.Service.exe. This vulnerability exists on any version of the Veeam Backup & Replication software prior to version 11a (build 11.0.1.1261 P20230227) and version 12 (build 12.0.0.1420 P20230223).
Infection Chain
The distribution and execution of BUGHATCH, a lightweight custom downloader most likely created by the Cuba ransomware group given it has only been observed being used by them in the wild, marks the start of the first stage. It connects to a command-and-control (C2) server and downloads the attacker’s preferred payload, which is often a tiny PE file or PowerShell script. Additionally, BUGHATCH has the ability to run files or instructions, including providing the operator with an option as to how a payload should be run.
Cuba operators used Metasploit to obtain a foothold in the target environment, especially to execute their dns_txt_query_exec payload that was hidden within the DLLs. They then proceeded to decode and run the shellcode in memory after being executed through certain exports. A DNS record or records are queried using a TXT query by the shellcode, which then executes the payload that is returned.
By employing the now-common BYOVD (Bring Your Own Vulnerable Driver) technique, Cuba disables endpoint security solutions. Additionally, it uses the “BurntCigar” module to terminate kernel processes associated with security products.
In addition to the recent Veeam vulnerability, Cuba also makes use of CVE-2020-1472 (“Zerologon”), a vulnerability in Microsoft’s NetLogon protocol that enables them to escalate privileges against AD domain controllers.
Cuba was seen employing different lolbins and Cobalt Strike beacons during the post-exploitation phase.
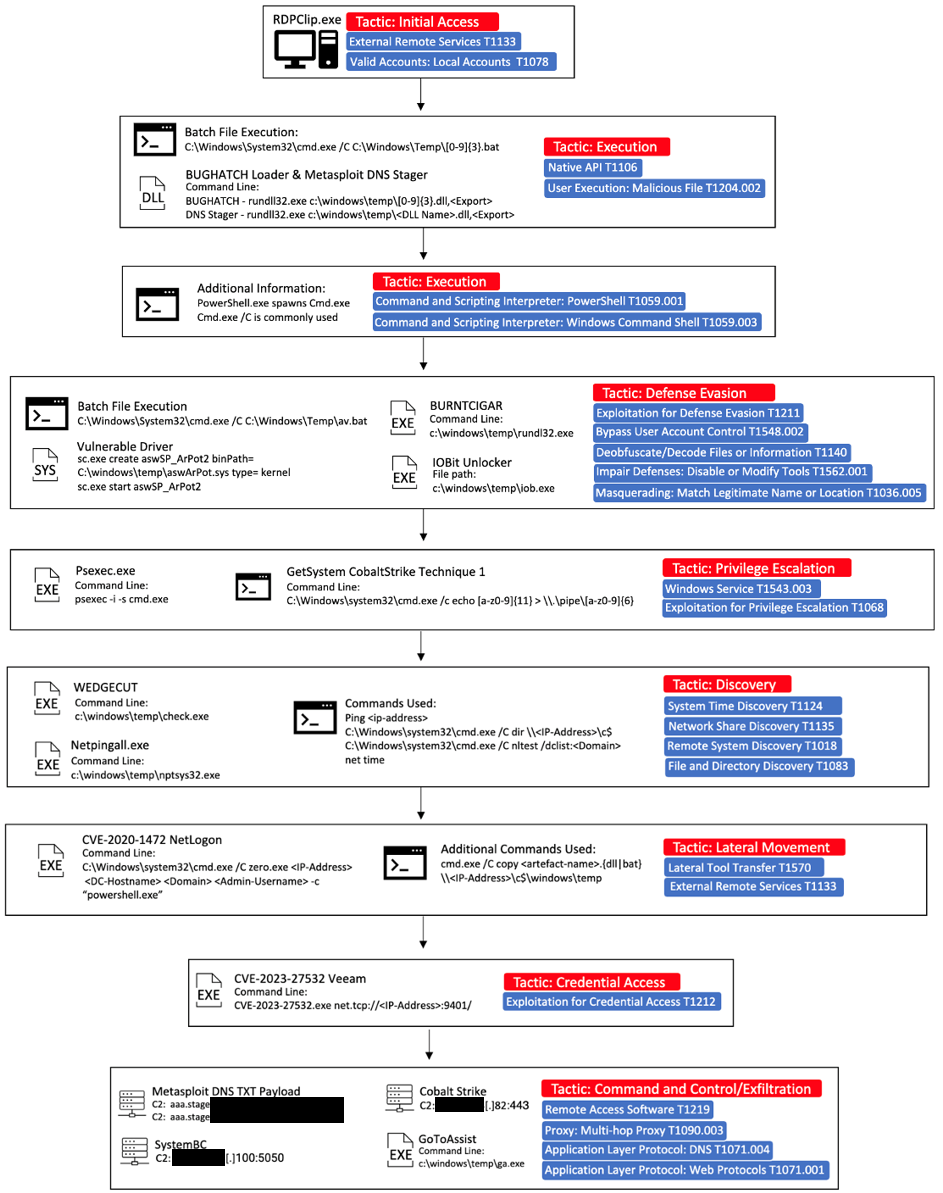
Infection Chain (Source: Blackberry)
MITRE ATT&CK
| Tactic | Technique |
| Initial Access | T1133, T1078.003 |
| Execution | T1106, T1204.002, T1059.001, T1059.003, T1569.002, T1218.011 |
| Defense Evasion | T1211, T1548.002, T1140, T1562.001, T1036.005 |
| Defense Evasion | T1211, T1548.002, T1140, T1562.001, T1036.005 |
| Privilege Escalation | T1543.003, T1068 |
| Discovery | T1124, T1135, T1018, T1083, T1057, T1016.001 |
| Lateral Movement | T1570, T1333 |
| Credential Access | T1212 |
| Command-and-Control | T1219, T1090.003, T1071.004, T1071.001, T1105 |
IOCs
58ba30052d249805caae0107a0e2a5a3cb85f3000ba5479fafb7767e2a5a78f3
3a8b7c1fe9bd9451c0a51e4122605efc98e7e4e13ed117139a13e4749e211ed0
cf87a44c575d391df668123b05c207eef04b91e54300d1cbbec2f48f5209d4a4
765d84ae85561bf5dbc1187da2b2cef91da9f222bcc6cf2c12cacd36e44bcffd
1c2d7f19f8c12e055e1ba8cdf5334e6cb5510847783fbe36121a35ad70f09eb3
9b1b15a3aacb0e786a608726c3abfc94968915cedcbd239ddf903c4a54bfcf0c
4b5229b3250c8c08b98cb710d6c056144271de099a57ae09f5d2097fc41bd4f1
075de997497262a9d105afeadaaefc6348b25ce0e0126505c24aa9396c251e85
bd93d88cb70f1e33ff83de4d084bb2b247d0b2a9cec61ae45745f2da85ca82d2
Fix Version: To safeguard your environment against CVE-2023-27532, you may upgrade to the below fix versions:
12 (build 12.0.0.1420 P20230223)
11a (build 11.0.1.1261 P20230227)
Prevention
Upgrade to the fix versions documented above.
- Password policies mandating strong keyspace and enabling multi-factor authentication for all critical services.
- Advanced endpoint security products on all endpoints to detect indicators of compromise (IOC) and take defensive action to block malicious payloads from executing.
- Keeping all operating systems and software up to date and conducting regular vulnerability scanning and penetration testing of all network infrastructure, remediating any discovered vulnerabilities as soon as possible.
- Implementing a principle of least privilege approach to security, including removing unnecessary access to administrative shares and other services.
- Segmented networks and NIPS and NIDS to monitor network activity for anomaly behavior.
- Hardening all endpoints, including employee workstations and servers, by disabling command-line and scripting activities and permissions and unrequired services to reduce the potential of a living off the land (LOTL)-type attacks.
- A solid backup strategy that includes offline, encrypted, and immutable backups of data.

