A recently fixed vulnerability (CVE-2022-47966) affecting Zoho ManageEngine ServiceDesk Plus has been used by Lazarus, a North Korean state-sponsored APT group, to spread the remote access trojan QuiteRAT.
Background
According to a report recently published by Cisco Talos, the attack began earlier this year. In the United States and the United Kingdom, it was intended to compromise suppliers of internet backbone infrastructure and healthcare organizations. Further investigation revealed that the attack was designed to distribute the QuiteRAT malware and a recently found remote access trojan (RAT), which the team named CollectionRAT.
Early in 2023, when the North Korean organization utilized an exploit for CVE-2022-47966, a pre-authentication remote code execution vulnerability impacting a number of Zoho ManageEngine products, Cisco Talos researchers learned about the attack against UK internet service providers.
Technical Analysis
CVE-2022-47966:
Unauthenticated RCE vulnerability CVE-2022-47966 affects Zoho ManageEngine products including ServiceDesk Plus, Password Manager Pro, and ADSelfService Plus. These products have been the target of public attacks during the previous 12 months. Depending on the specific ManageEngine product and whether or not its SAML single-sign-on is active, or has ever been enabled, the vulnerability—a pre-authentication remote code execution—can be exploited. The usage of Apache xmlsec 1.4.1, often known as XML Security for Java, is responsible for this.
QuiteRAT:
The researchers classified QuiteRAT, which was discovered in February 2023, as a successor of MagicRAT, a remote access trojan that the North Korean group also used in the second half of 2022 to target energy suppliers in Japan, Canada, and the United States. Averaging about 4 to 5 MB in size, QuiteRAT is a lot smaller implementation than MagicRAT, which is a larger, bulkier malware family.
This substantial difference in size is caused by the fact that Lazarus Group only incorporated a small subset of the necessary Qt libraries into QuiteRAT as compared to the whole Qt framework in MagicRAT. Furthermore, QuiteRAT lacks a persistence capability and requires one to be provided by the C2 server in order to continue operating on the infected endpoint, in contrast to MagicRAT, which has persistence mechanisms built into it via the ability to set up scheduled activities. This is another element that contributes to QuiteRAT’s lower size.
The inclusion of Qt increases the complexity of the code, which makes human analysis more difficult, as shown with the MagicRAT malware from Lazarus Group. Since Qt is rarely utilized in malware development, using it significantly reduces the accuracy of machine learning and heuristic analysis detection.
Capabilities of QuiteRAT include Self-deletion, Launching and fetching new payloads, New process spawning, Reverse shell creation, System information gathering, File management, and Arbitrary command execution.
The group’s penchant for reusing infrastructure not only allowed researchers to link these most recent attacks to Lazarus but also allowed them to identify additional malware they utilize (notably, CollectionRAT).
CollectionRAT:
According to a different report from Cisco Talos, the North Korean hacking group is using a new malware dubbed CollectionRAT, which the research team found after looking at the infrastructure, the attackers had previously used in past attacks.
CollectionRAT is a Windows binary that is bundled with the Microsoft Foundation Class (MFC) library and instantly decrypts and runs the malicious code. The researchers said that MFC, which is typically used to design the user interfaces, controls, and events for Windows applications, “allows many components of malware to smoothly operate with one other while abstracting the core implementations of the Windows OS from the authors.
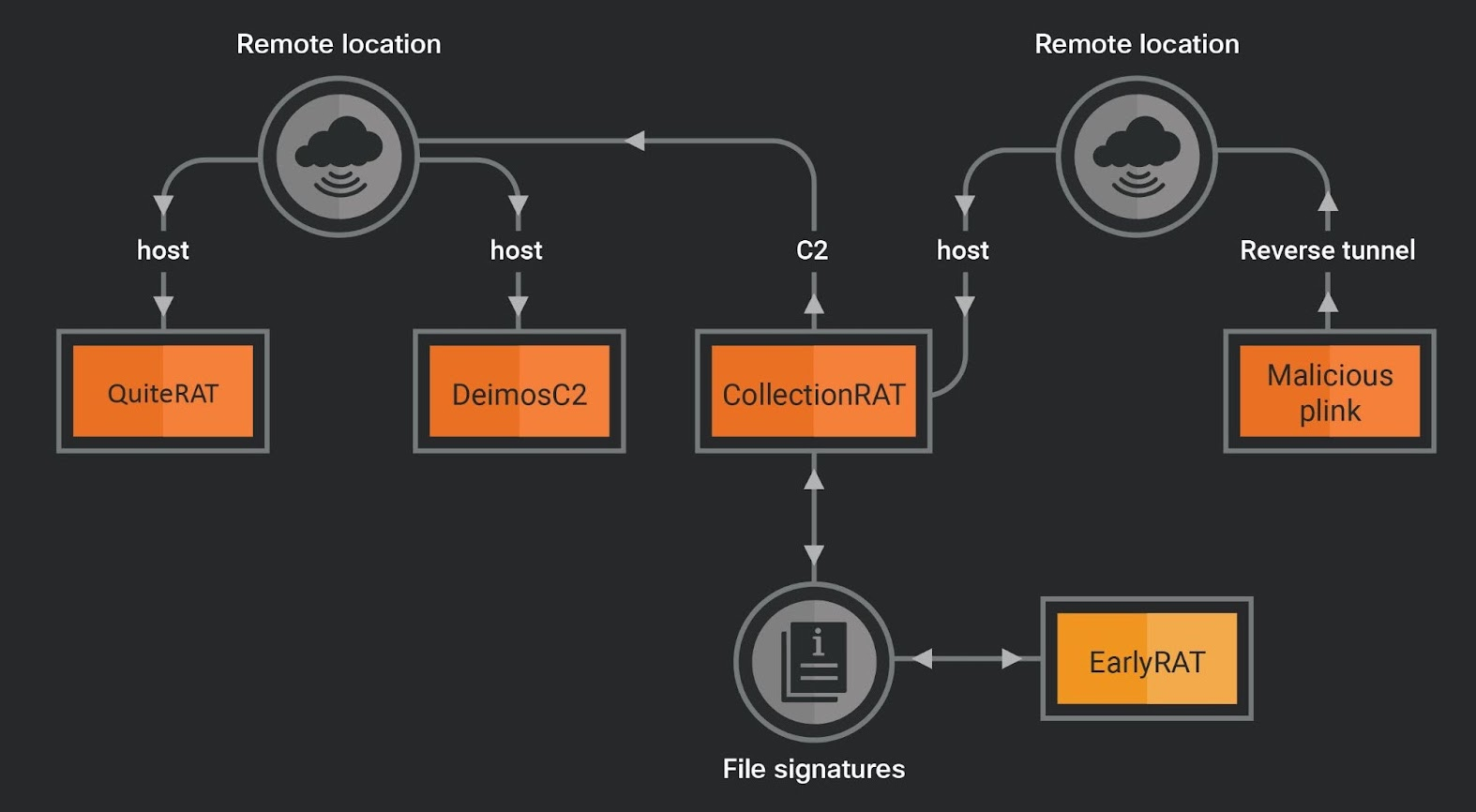
Operational links between the various malware implants. (Source: Talos)
The extensive use of open-source tools and frameworks, such as DeimosC2 for control and command communication, PuTTY Link (Plink) for remote tunneling, and Mimikatz for credential theft, are among the additional indications of evolution in the North Korean group’s procedures, techniques, and tactics that Cisco has listed.
Infection Chain:
QuiteRAT:
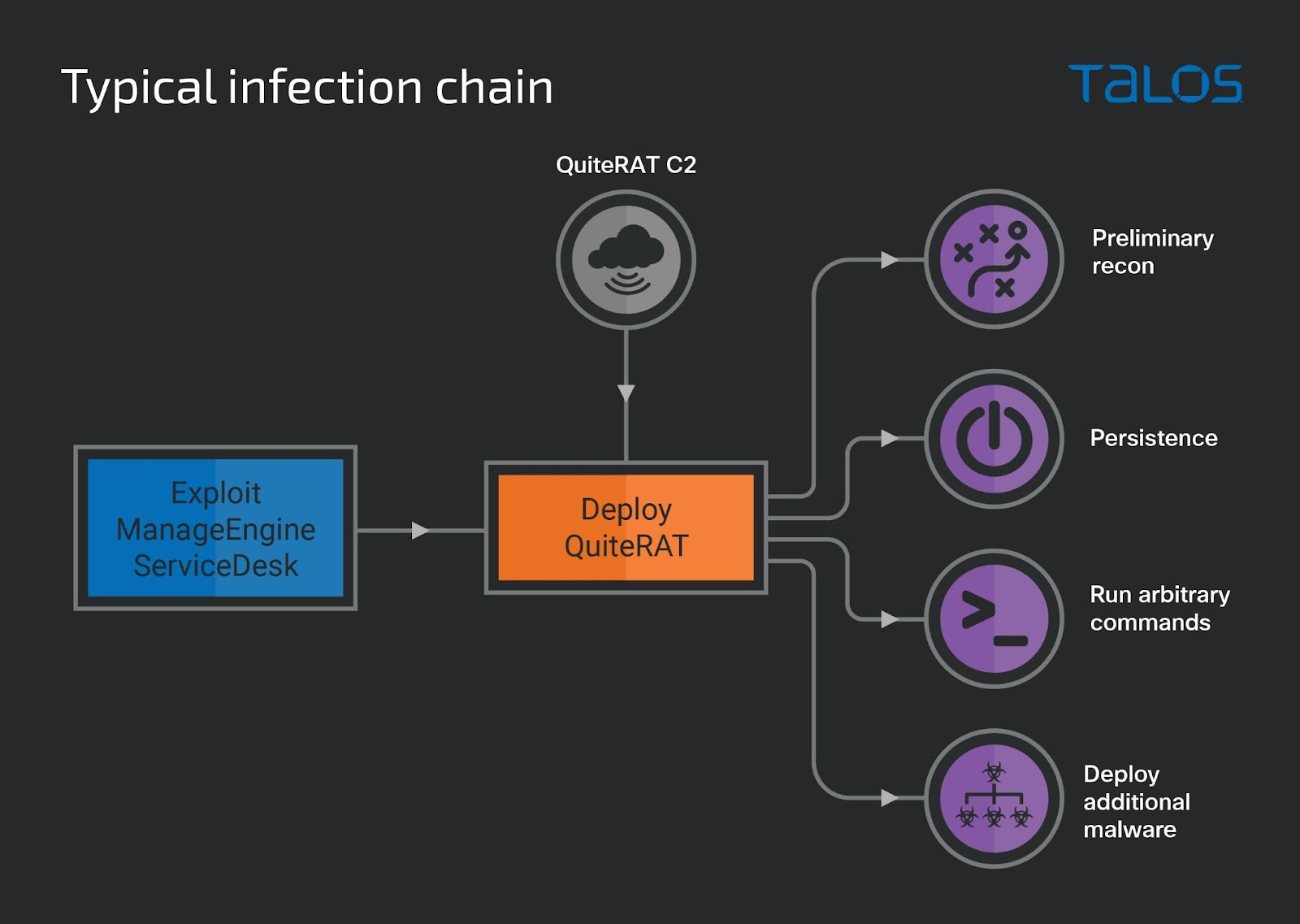
To get started, the actors used a ManageEngine ServiceDesk instance that was vulnerable. The successful attack caused the Java runtime process to immediately download and launch a malicious payload. If the malware is downloaded successfully, the Java process will then execute the QuiteRAT binary, activating the implant on the compromised server. As soon as the implant begins to operate, it sends out basic system data to its command and control (C2) servers and then waits for a response from the C2 with either a command code to execute or an actual Windows command to execute on the endpoint through a child cmd.exe process.
There is no in-built persistence mechanism in QuiteRAT. Persistence for the implant is achieved via the registry by issuing the following command to QuiteRAT:
C:\Windows\system32\cmd[.]exe /c sc create WindowsNotification type= own type= interact start= auto error= ignore binpath= cmd /K start c:\users\public\notify[.]exe
Infection chain (Source: Talos)
CollectionRAT:
In the beginning, CollectionRAT collects system data in order to fingerprint the infection and transmit it to the C2 server. It then gets instructions from the C2 server to carry out a number of actions on the compromised machine. In order to execute arbitrary instructions on the system, the implant has the capacity to build a reverse shell. The implant has the ability to download and launch additional payloads since it can read and write files from the disc and spawn new processes. When instructed by the C2, the implant can also delete itself from the endpoint.
To register the infection, the basic system data is transferred to the C2 server, which then sends instructions to the implant.
IOCs:
ed8ec7a8dd089019cfd29143f008fa0951c56a35d73b2e1b274315152d0c0ee6
db6a9934570fa98a93a979e7e0e218e0c9710e5a787b18c6948f2eedd9338984
773760fd71d52457ba53a314f15dddb1a74e8b2f5a90e5e150dea48a21aa76df
05e9fe8e9e693cb073ba82096c291145c953ca3a3f8b3974f9c66d15c1a3a11d
e3027062e602c5d1812c039739e2f93fc78341a67b77692567a4690935123abe
146[.]4[.]21[.]94
109[.]248[.]150[.]13
108[.]61[.]186[.]55:443
hxxp[://]146[.]4[.]21[.]94/tmp/tmp/comp[.]dat
hxxp[://]146[.]4[.]21[.]94/tmp/tmp/log[.]php
hxxp[://]146[.]4[.]21[.]94/tmp/tmp/logs[.]php
hxxp[://]ec2-15-207-207-64[.]ap-south-1[.]compute[.]amazonaws[.]com/resource/main/rawmail[.]php
hxxp[://]109[.]248[.]150[.]13/EsaFin[.]exe
hxxp[://]146[.]4[.]21[.]94/boards/boardindex[.]php
hxxp[://]146[.]4[.]21[.]94/editor/common/cmod