The VMware Aria management and monitoring package provides full-scope operations management, IT automation, log management, analytics creation, network visibility, and capacity planning for virtualized environments and hybrid clouds.
Overview:
Two vulnerabilities in Aria Operations for Networks were addressed by VMware this week. The first vulnerability, CVE-2023-34039, is an authentication bypass vulnerability caused by a lack of distinct cryptographic key generation, according to VMware. It has a CVSS score of 9.8. The second vulnerability, CVE-2023-20890, is an arbitrary write file vulnerability with a CVSS score of 7.2.
Technical details:
VMware Aria Operations for Networks, formerly known as vRealize Network Insight, contains a critical authentication bypass vulnerability (CVE-2023-34039) scoring a worrisome 9.8 on the CVSS scale, which was publicly disclosed by VMware on Tuesday, August 29, 2023. If exploited, this vulnerability could allow a threat actor to bypass SSH authentication and gain access to the Aria Operations for Networks CLI.
An attacker may bypass SSH authentication with just the bare minimum of tools, such as network access to Aria Operations for Networks. Giving them unrestricted access to the Aria Operations for Networks Command Line Interface (CLI) would be equivalent to this circumstance. The consequences are severe, including the potential disclosure of confidential information and risk to a company’s security system.
CVE-2023-20890 is a vulnerability that permits arbitrary file writes and was discovered by Sina Kheirkhah of the Summoning Team. With a CVSS rating of 7.2, CVE-2023-20890 is still considered to be very dangerous. An authorized person with administrative rights can use this vulnerability to secretly write files to any desired location. This arbitrary file write vulnerability is similar to an unlocked side backdoor that may be used to remotely execute code on the exposed device.
Two days after revealing the serious security vulnerability, VMware acknowledged that the CVE-2023-34039 exploit had been publicly released online.
The proof-of-concept (PoC) attack affects all versions 6.0 through 6.10 of Aria Operations for Networks.
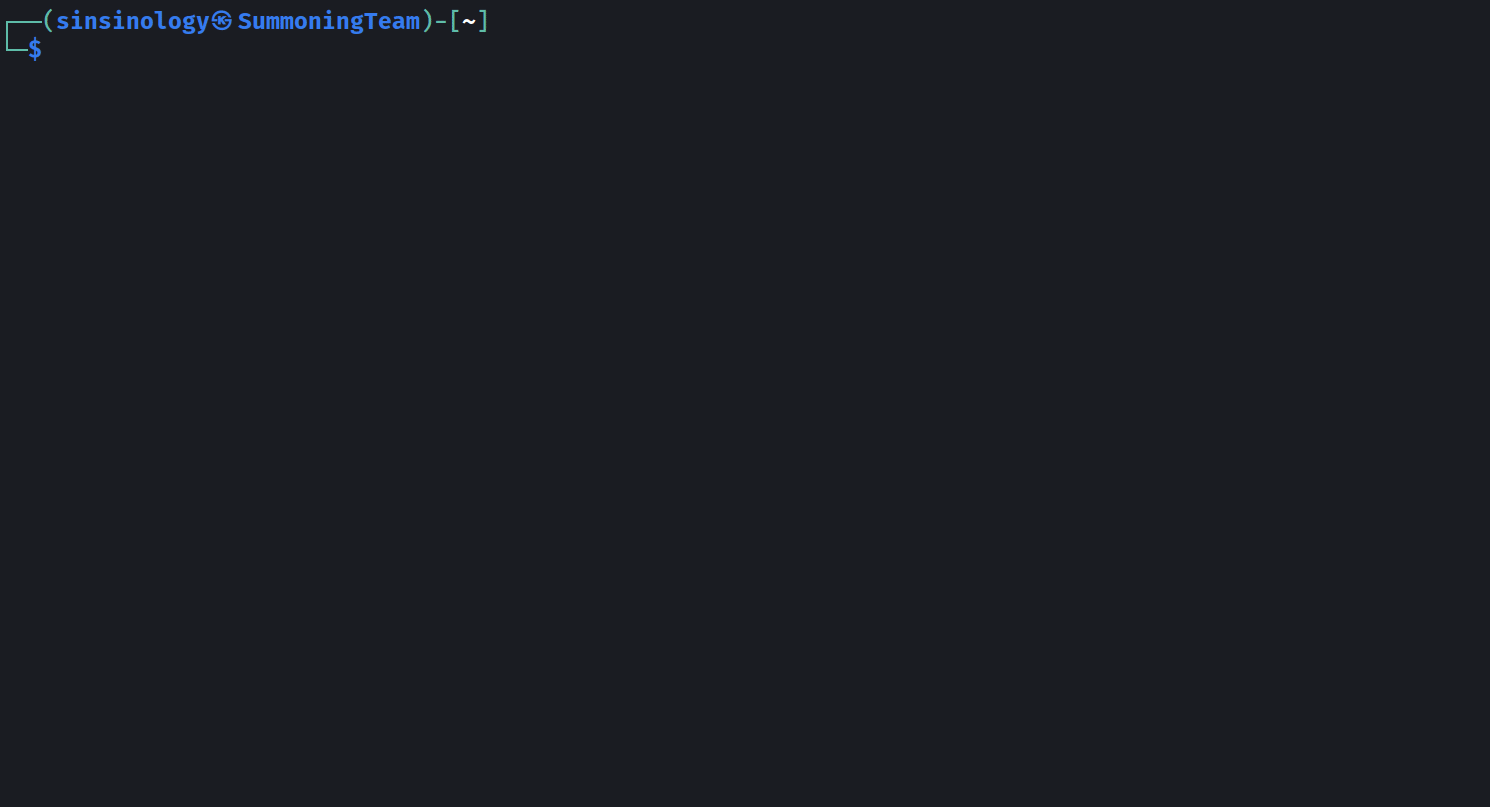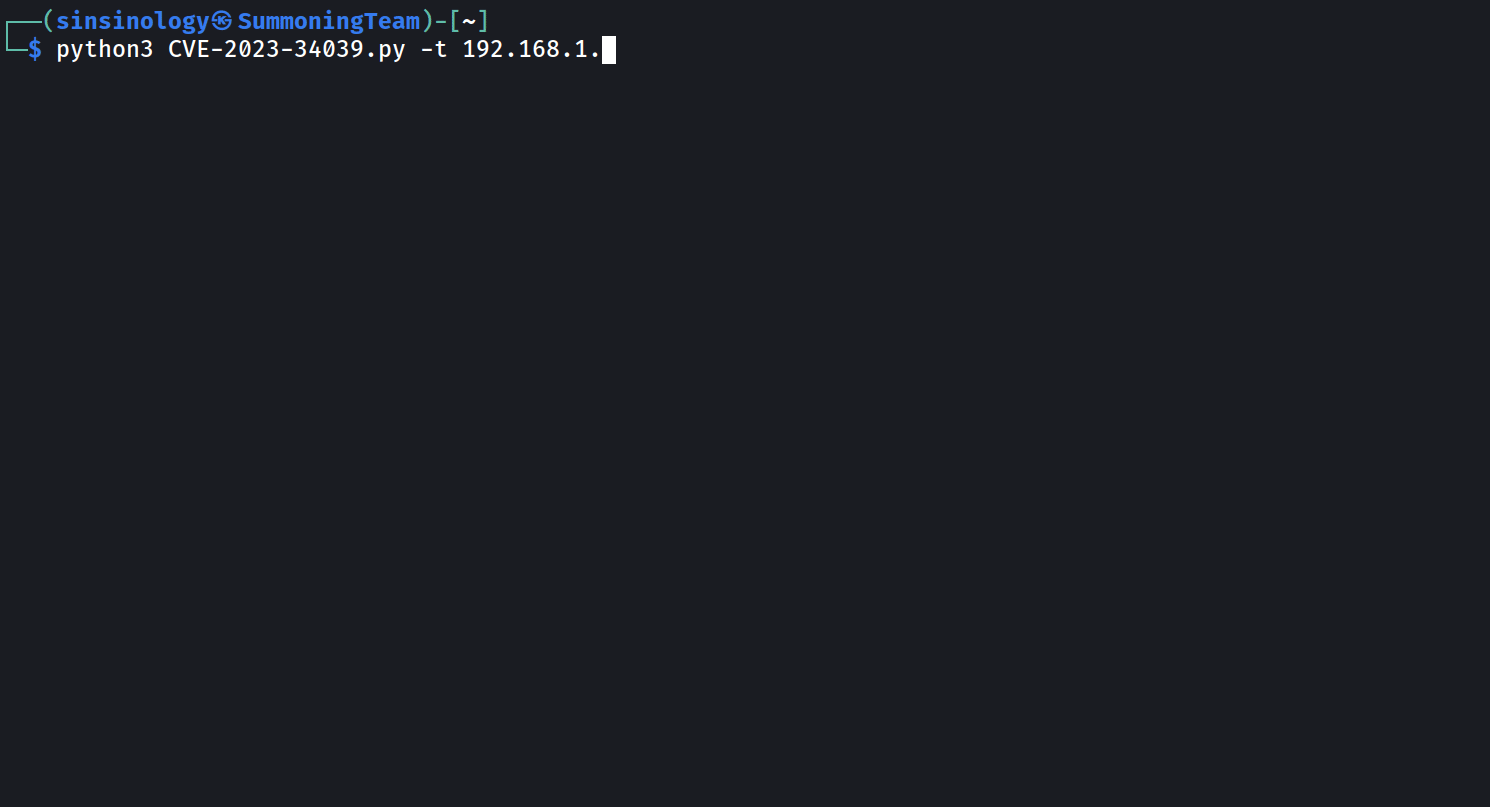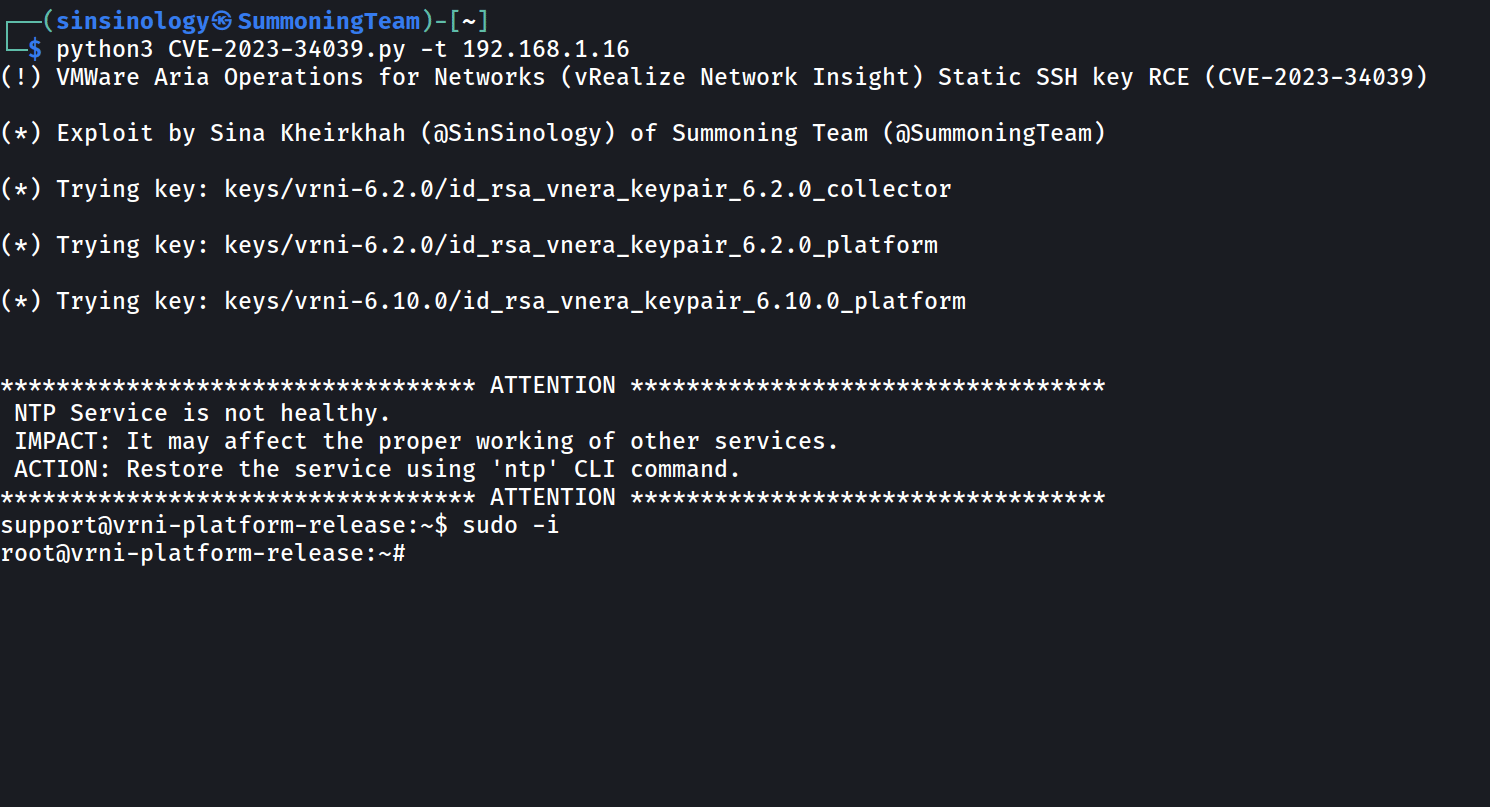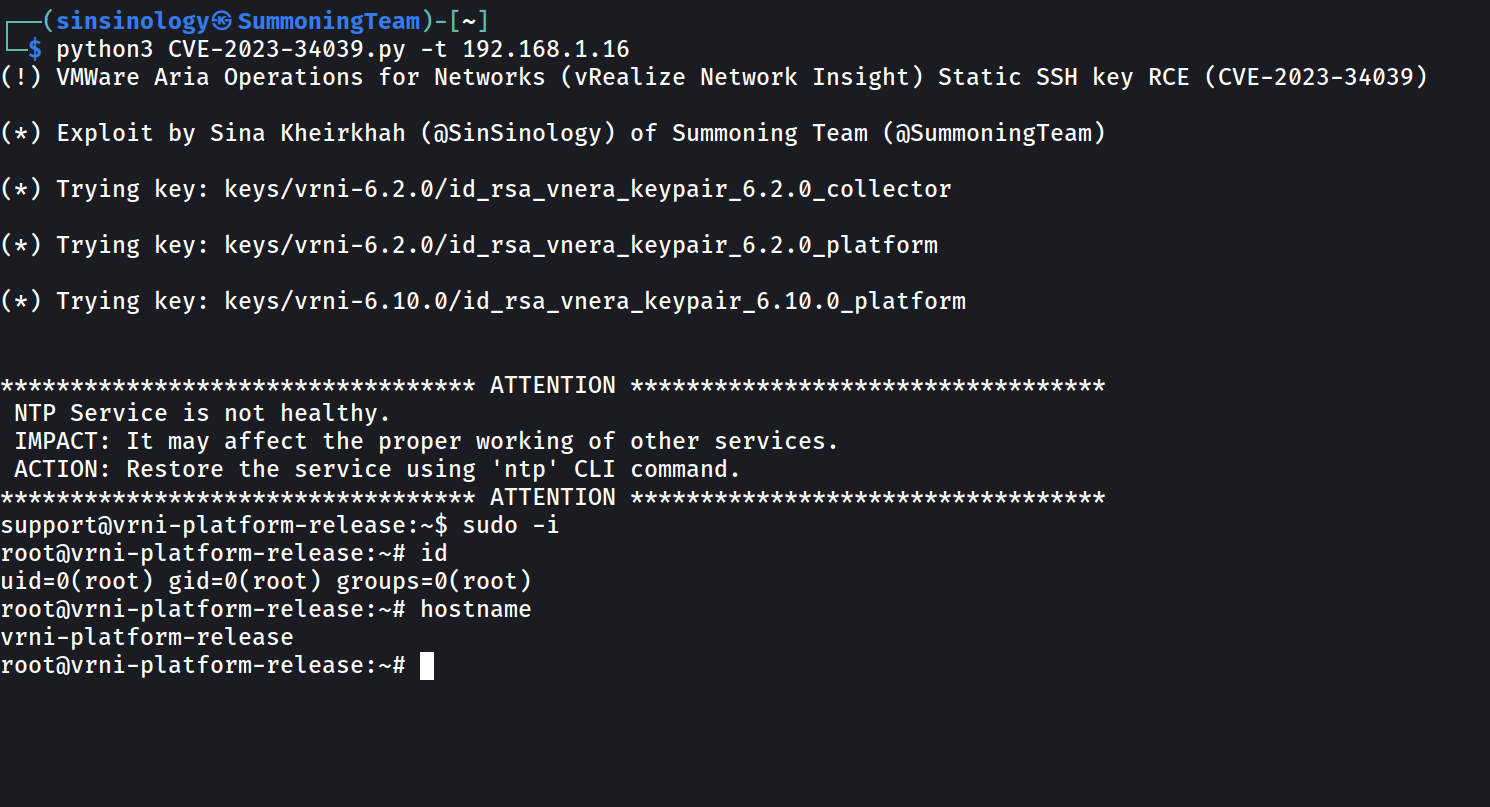
According to Kheirkhah, the underlying source of the problem is hardcoded SSH keys that were left behind when VMware neglected to regenerate SSH-authorised keys. All keys from various versions of this product were gathered to construct an exploit k that is entirely functioning.
The POC is available on github and can be accessible from https://github.com/sinsinology/CVE-2023-34039
CVE-2023-34039 PoC exploit (Source: Summoning Team)
Affected versions:
| VMware Aria Operations for Network | |
|---|---|
| Affected Versions | Fixed Version |
| 6.x | 6.11 (KB94152) |
| 6.2.0 | Build number: 1688977536 |
| 6.3.0 | Build number: 1688986302 |
| 6.4.0 | Build number: 1689079386 |
| 6.5.1 | Build number: 1688974096 |
| 6.6.0 | Build number: 1688979729 |
| 6.7.0 | Build number: 1688972173 |
| 6.8.0 | Build number: 1688989059 |
| 6.9.0 | Build number: 1688995771 |
| 6.10.0 | Build number: 1692934256 |
Recommendations:
Through the release of VMware Aria Operations Networks 6.11, VMware has fixed these vulnerabilities. To protect oneself from these vulnerabilities, VMware strongly urges its users to immediately update to version 6.11 of VMware Aria Operations Networks.
The well-known virtualization services provider has said that both of these vulnerabilities are fixed in version 6.11.0. Since hackers and threat actors have historically found security flaws in VMware to be alluring, users must act promptly to upgrade to the most recent version of the software in order to protect themselves from possible attacks.