Phishing attacks are still one of the most prevalent methods for threat actors to get access, and they pose a serious risk to an organization’s digital assets.
Background:
Social engineering techniques are frequently used in phishing attempts to get around security mechanisms and trick people into clicking links, downloading files, or giving out private information. It is a cyberattack that requires little work but yields many results.
The risk posed by the InterPlanetary File System (IPFS) increases along with its popularity. The adoption of IPFS, which was first established in 2015 utilizing Web 3.0 technology, is largely motivated by data privacy and a desire to lessen dependency on centralized giant tech companies like Google, Microsoft, Facebook, etc. Unfortunately, as adoption rates climb, so do the number of threat actors who have seized the opportunity to weaponize IPFS technology over the past few years in order to grow their cybercrime operations.
InterPlanetary File System (IPFS):
The modular set of protocols known as IPFS facilitates data organization and transfer. Although the primary use case for IPFS is for decentralized data publication (files, directories, webpages, etc.), there are several implementations of this open-source technology.
Users from all across the world can share files using the peer-to-peer distributed file system known as IPFS (InterPlanetary File System). Instead of using file paths for addressing like centralized systems do, IPFS uses unique content identifiers (CID). The CID is created using the file’s hash value and added to a distributed hash table along with the file owner’s information. The actual file is downloaded straight from the computer belonging to the user who “uploaded” it to IPFS. The BitTorrent protocol, which is also a distributed network in which file sharing occurs directly between user devices, has a topology that is somewhat reminiscent of IPFS.
Since content on IPFS is kept on multiple nodes rather than a single central location, removing it is significantly more difficult than on centralized file storage sites. Content on IPFS needs to be deleted from every node in order to be removed. As a result, IPFS is prone to being utilized maliciously.
There are two types of IPFS links, the Path Gateway and Subdomain Gateway [1].
Path Gateways have a fixed domain/host and identify the IPFS resource through a resource-identifying string in the path. The Path Gateway has the following structure:
- https://.tld/ipfs//path/to/resource
- https://.tld/ipns/<dnslink/ipnsid>/path/to/resource
On the other hand, Subdomain Gateways have a resource-identifying string in the subdomain. Subdomain Gateways have the following structure:
- https://.ipfs..tld/path/to/resource
One gateway domain serves the same role as any other, which means attackers can easily change the gateways that are used.
Use of IPFS in Phishing:
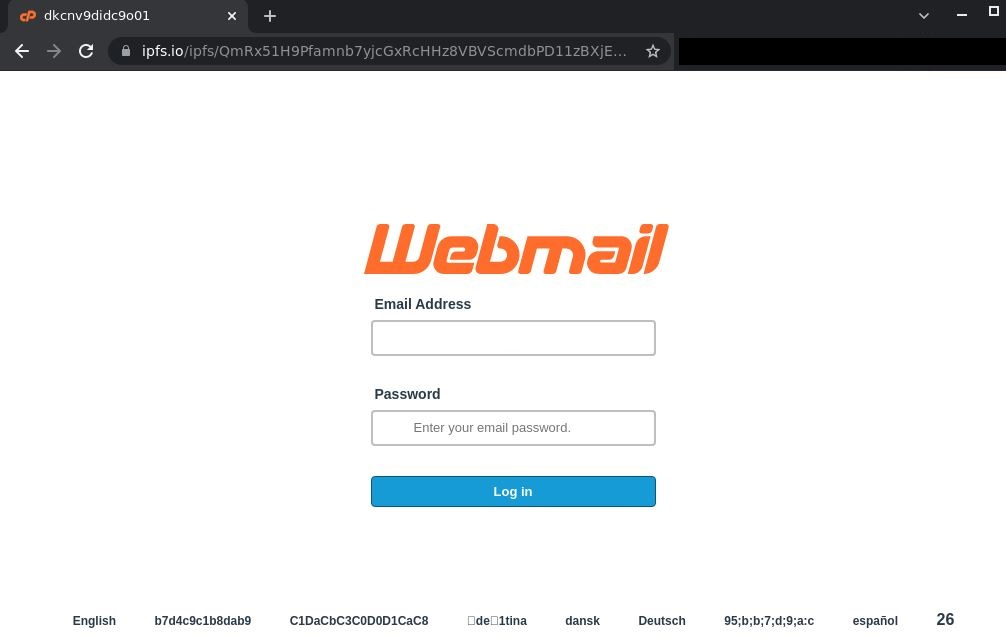
Scammers started extensively utilizing IPFS for email phishing attacks in 2022. In order for victims to open the file, regardless of whether they had an IPFS client installed on their devices, attackers would upload HTML files containing phishing forms to IPFS and employ gateways as proxies. Through a gateway, the hackers would insert file access URLs inside phishing messages sent to potential victims.
A distributed file system is used by attackers to reduce the cost of hosting phishing pages. Additionally, IPFS does not allow the deletion of files uploaded by third parties. One can request that a file’s owners delete it if they want it to totally disappear from the system, but thieves will almost certainly never comply.
Although P2P networks dominate the distribution of IPFS, regular web users can access IPFS through a number of public IPFS gateways, such as ipfs.io or dweb.link. You can access files on the IPFS network without launching an IPFS client thanks to the proxies that these scammers utilize.
Phishing page used in a targeted attack
Mitigation:
- Always keep your browsers and software updated with the latest security patches.
- Try to manually insert URLs or use bookmarked links. Otherwise, properly inspect links to ensure they match the legitimate site.
- Use two-factor authentication (2FA) whenever possible to protect your accounts from unauthorized access.
- Ensure you only use trustworthy IPFS gateways. Avoid unknown gateways.
- Protect your devices using up-to-date antivirus products.
- Always verify instructions in emails, texts, or DMs via official communication channels, especially if they are random or out of the blue.
- Check every IPFS gateway’s SSL certificate. Alternatively, you can install IPFS Companion to securely interact with the network through your browser.
- When using IPFS gateways, you can employ a virtual private network (VPN) to mask your private address. Note that VPNs won’t be effective if you run an IPFS node.
- Use DNS sinkholing or web filters to block IPFS-based phishing sites.
- Stay up-to-date on IPFS trends, as cybercriminals will likely invent more sophisticated techniques to aid their malicious agendas.