NSFOCUS researchers examined the DarkCasino attack pattern, which exploited the WinRAR zero-day vulnerability identified as CVE-2023-38831. The financially motivated APT group conducted phishing operations against forum participants via online trading forum posts using specially generated archives.
Background:
When tracking the exploitation of WinRAR vulnerabilities, NSFOCUS Research Labs discovered a large number of attacks by known APT organizations as well as unconfirmed attackers. The majority of these attacks were directed at national governments or global organizations.
APT DarkCasino:
DarkCasino is a financially driven APT group first discovered in 2021. The term DarkCasino is derived from a large-scale APT attack of the same name that was intercepted by NSFOCUS Research Labs in 2022. DarkCasino’s APT group primarily targets various online trade platforms in Europe, Asia, the Middle East, and other countries, including cryptocurrency, online casinos, network banks, and online credit platforms. DarkCasino is skilled at acquiring credentials from target hosts in order to get assets put by victims in online accounts.
DarkCasino is an APT threat actor with high technical and learning capabilities, and it excels at incorporating popular APT attack methods into its assault process. DarkCasino initially based its phishing attempts on the attack concept of an APT attacker dubbed Evilnum, employing malicious shortcuts, image steganography, and other technologies. Because the overall process design was similar to that of Evilnum, NSFOCUS Research Labs once attributed this organization to Evilnum; however, after H2 2022, DarkCasino gradually abandoned the Evilnum-borrowed attack idea and developed a set of multi-level loading patterns based on several Visual Basic components, allowing it to implement many larger-scale network attacks.
CVE-2023-38831:
CVE-2023-38831 is an arbitrary execution vulnerability in WinRAR software that was exploited in April 2023 by DarkCasino and addressed in WinRAR v6.23 in August 2023.
CVE-2023-38831 is based on the file running mechanism of the WinRAR software. It spoofs the API function ShellExecuteExW called by WinRAR by constructing a decoy file, a folder with the same name as the decoy file, and a malicious file with the same name with a space at the end of the folder, allowing it to release and execute the malicious file when the decoy file should have been opened.
Exploitation of CVE-2023-38831:
DarkCasino created a new attack pattern and launched a fresh round of attacks targeting internet trading forums in April 2023. In this new attack pattern, DarkCasino used a WinRAR zero-day vulnerability to place malicious programs within specially created vulnerability zip files for phishing attacks against forum participants via online trading forum posts.
NSFOCUS Research Labs discovered that DarkCasino used these vulnerabilities to compress files, resulting in two attack processes. The core logic of these two attack procedures is nearly identical, with the key difference being the Trojan data storage format.
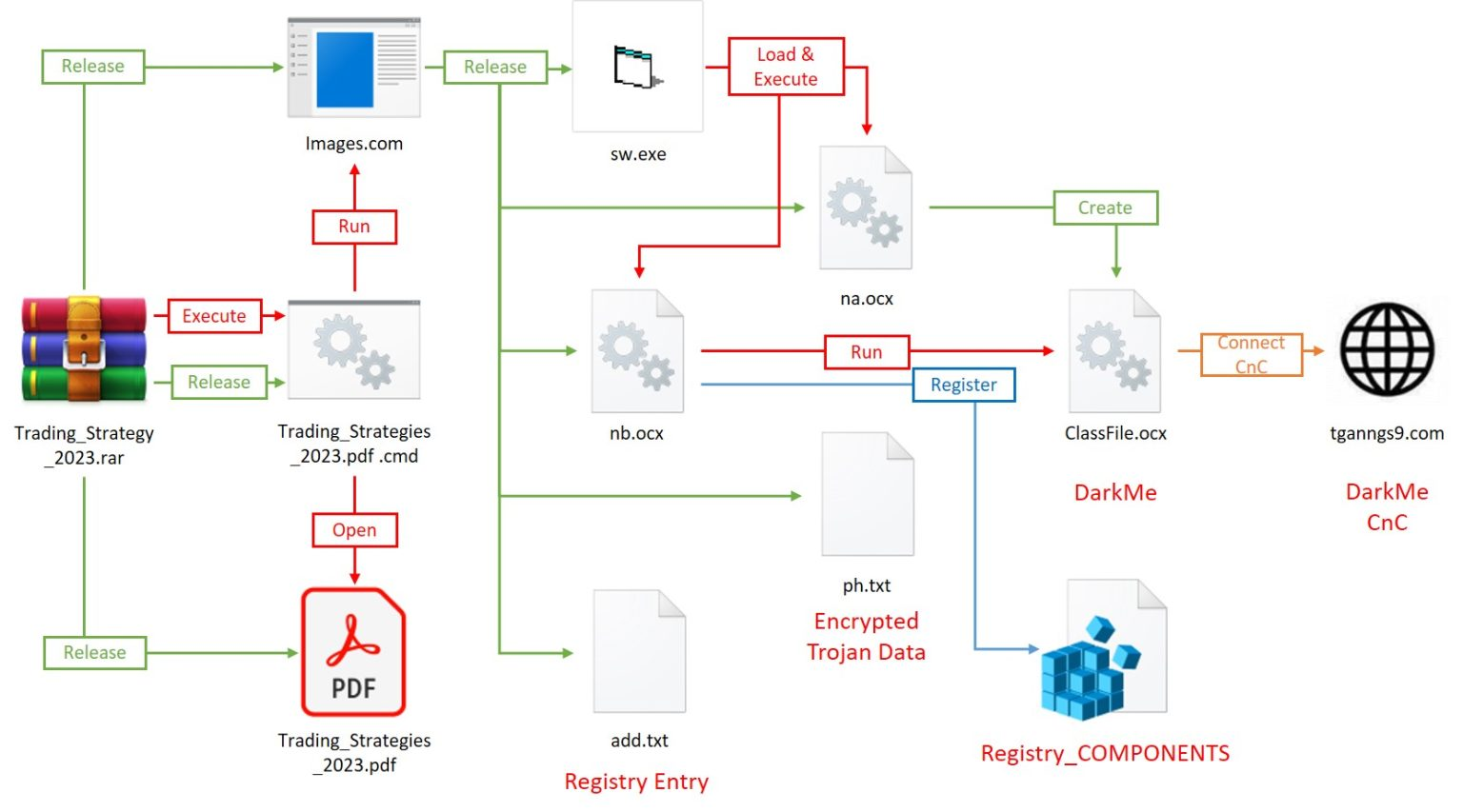
The following diagram depicts the primary components of this attack procedure, which include the CVE-2023-38831 vulnerability exploitation file, Cabinet archive file, registry file, and ActiveX control file. There are three stages to it: vulnerability exploitation, load release, and Trojan execution.
Fig. Attack Process of DarkCasino (NSFocus)
When NSFOCUS Research Labs examined the impact surface of vulnerability CVE-2023-38831, it discovered that since the vulnerability’s disclosure in August 2023, multiple APT organizations and unconfirmed attackers have used it for phishing attacks, the majority of which target important government agencies in various countries.
NSFOCUS Research Labs also discovered a huge number of exploitation files created and distributed by phishing email hackers around the world, indicating that the vulnerability has been widely abused.
Multiple threat actors have joined the CVE-2023-38831 exploitation bandwagon in recent months, including APT28, APT29, APT40, Dark Pink, Ghostwriter, Konni, and Sandworm.
Recommendations:
- This vulnerability affects all versions of WinRAR prior to 6.23. It is recommended that you update WinRAR to the most recent version. Updating your software applications, browsers, and gadgets on a regular basis is an important security practice that can help protect your systems against known vulnerabilities and cyber threats.
- Conduct simulated attack scenarios to ensure that staff are aware of phishing and other threats and that incidents are reported to the internal cybersecurity team.
- Segment the network to keep critical systems and sensitive data separate from the rest of the network. This helps to limit potential breaches and reduces attacker lateral movement.
- Proper logging, asset visibility, and system monitoring are critical components of a strong cybersecurity strategy. These methods give a network overview and aid in the detection of anomalies that may signal a security threat.
IOCs:
| Hash | APT Group |
|---|---|
| dd9146bf793ac34de3825bdabcd9f0f3 | DarkPink |
| 5504799eb0e7c186afcb07f7f50775b2 | DarkPink |
| c5331b30587dcaf94bfde94040d4fc89 | DarkPink |
| ac28e93dbf337e8d1cc14a3e7352f061 | DarkPink |
| fefe7fb2072d755b0bfdf74aa7c9013e | DarkPink |
| 428a12518cea41ef7c57398c69458c52 | Konni |
| 7bb106966f6f8733bb4cc5bf2ab2bab4 | GhostWriter |
| 2b02523231105ff17ea07b0a7768f3fd | Actor230830 |
| 63085b0b7cc5bb00859aba105cbb40b1 | Actor231003 |
| 7195be63a58eaad9fc87760c40e8d59d | Actor231004 |
| 129ccb333ff92269a8f3f0e95a0338ba | Actor231010 |
| cd1f48df9712b984c6eee3056866209a | Actor231010 |
| b05960a5e1c1a239b785f0a42178e1df | Actor231010 |
| 6b5d5e73926696a6671c73437cedd23c | Actor231009 |