Based on the Go programming language, JinxLoader is a recently found malware loader that fraud-related actors are now using to spread following payloads, such as Formbook and its XLoader sequel.
Background:
The threat actors use a number of multi-step attack approaches, which cybersecurity experts have identified. Phishing attacks are the main way that JinxLoader is deployed.
Infection Chain:
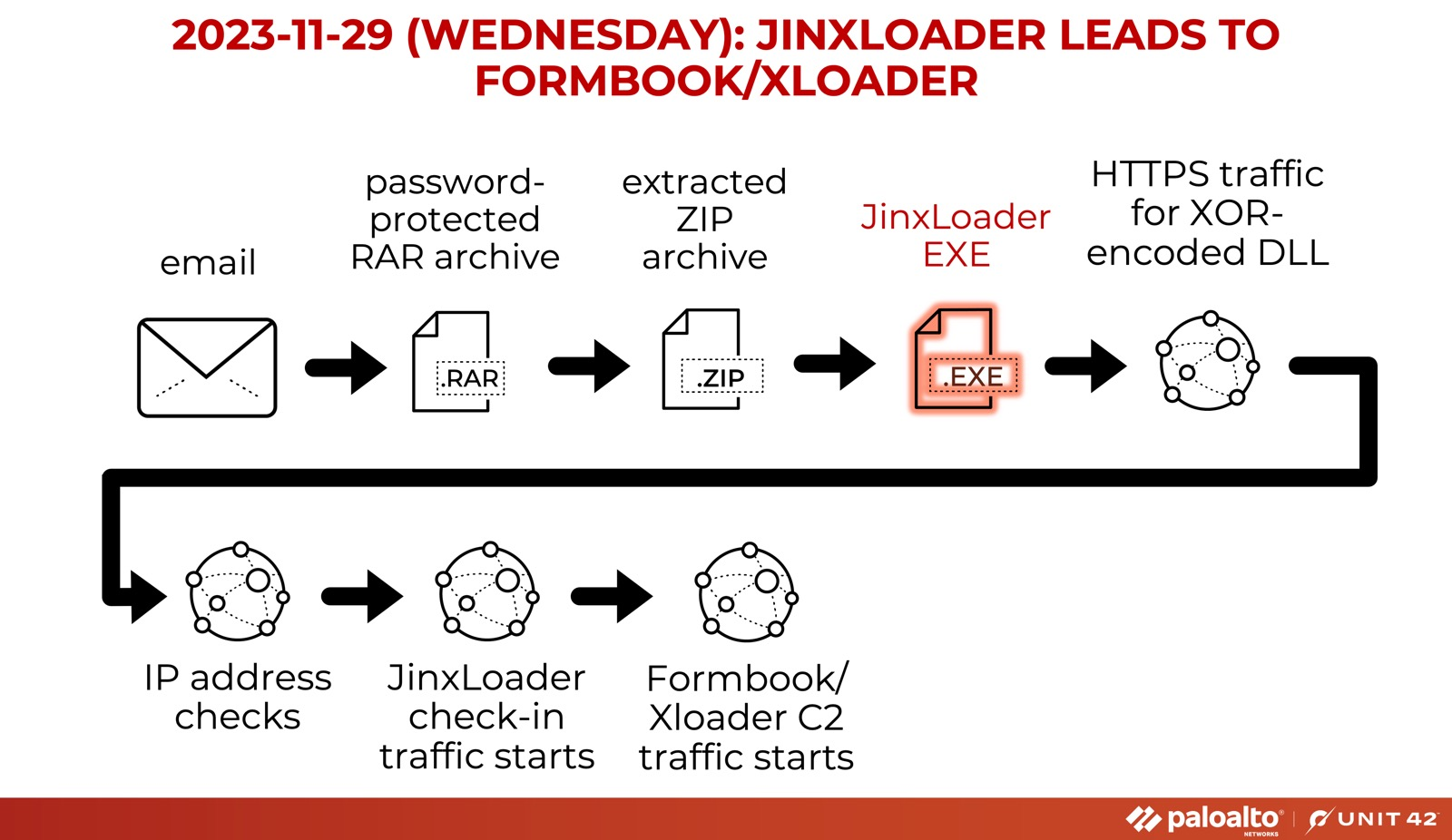
The malware was initially discovered by Palo Alto Networks’ Unit 42 in November 2023, and they reported that it had been promoted on the hacker forum Hackforums since April 30, 2023. The researchers detected an attack that employed phishing communications purporting to be from the Abu Dhabi National Oil Company (ADNOC). The mail’s contents were an attempt to deceive the recipients into opening a RAR archive that required a password. The infection chain begins as soon as the archive is opened, leading to the JinxLoader payload being deployed.
Fig. Infection chain (Source: Unit42)
2023-11-29 (Wednesday): Email –> #JinxLoader –> #Formbook/#XLoader – IOCs available at https://t.co/pkII3mJ0f3 – Of note, #JinxLoader is a relatively new malware service first posted to hackforums[.]net on 2023-04-30.#Unit42ThreatIntel #TimelyThreatIntel #Wireshark pic.twitter.com/buM9OQeI4G
— Unit 42 (@Unit42_Intel) November 30, 2023
The primary function of JinxLoader is obvious: it is a tool for loading and running malware onto computers that are intended for other purposes.
“Stolen information will be archived and uploaded to Gofile or Anonfiles; the malware will also post it onto the author’s Discord using webhooks,” Symantec said. “It’s also capable of posting to Telegram via a Telegram bot.”
IOCs:
SHA256 hash:
08bf78e0c3c6250a295664c3fb4be7d05b90592260f979f87bb476638dd4a0a9
c1d3ad3f518cf02925d304f1912860d01e8cfd8d2ed6f76bd200c7d25370206f
edf824f5152829ef7be198c97a42e4ecd5ae9be37ef57051deda0435cc302063
5c11e9204d181a28fb6ba97d0f26febe409e2151ae71c5aa63ea34ffb14ed383
9b1090ff32a441a89294739884b9a0330e75497573dde39b6b79ac4dd0a9effd
b7c66440c975bed86efe68c47c95bd1460ab8cf21bccacfc1e80c145e7be0f8b
INFECTION TRAFFIC:hxxps://www.wgs[.]com[.]pk/js/Qvaloe.vdf
ipinfo[.]io HTTPS traffic (IP address check, not inherently malicious)
checkip.amazonaws[.]com HTTPS traffic (IP address check, not inherently malicious)
46.183.221[.]59 port 80 – 46.183.221[.]59 – POST / HTTP/1.1 (application/x-www-form-urlencoded)
DOMAINS USED IN FORMBOOK/XLOADER C2 TRAFFIC:
www.1214888[.]com
www.219855[.]xn--80aswg
www.autrevalevale[.]click
www.austintrafficlawyer[.]com
www.cjjmobbbshhhu[.]shop
www.e3iaibr[.]icu
www.infinite-7[.]com
www.julieannmirabel[.]online
www.ldhqi4[.]fun
www.ncdanmark[.]org
www.ofupakoshi[.]com
www.overthemoonphoto[.]com
www.taxhwangeub[.]com
www.terranovaservices[.]top
www.worldlife[.]casino
www.zkrbma[.]store