Remote Desktop Software AnyDesk recently faced a cyberattack. On February 1st, 2024, AnyDesk revealed that a cyber attack had allowed hackers to get access to the company’s production server and reset its password.
Incident:
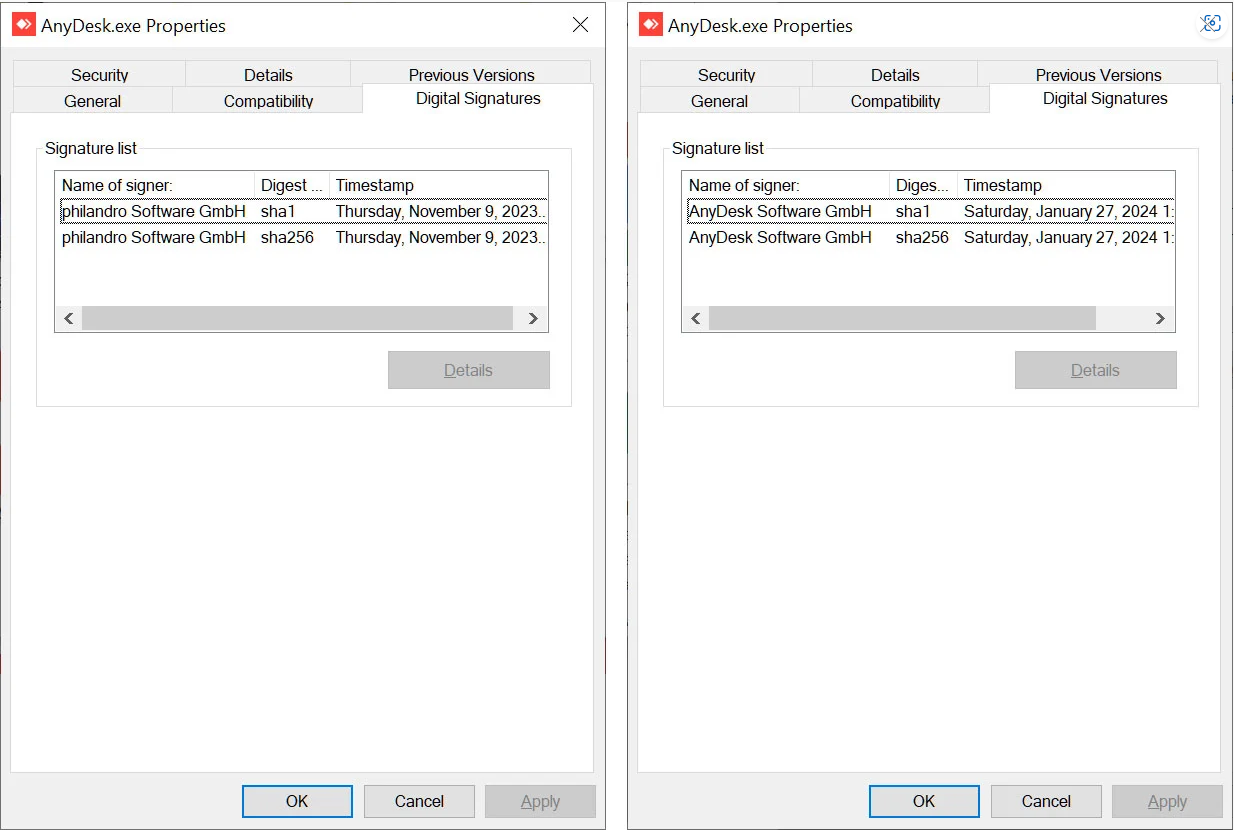
The attackers stole both the source code and the private code signing keys. (Software developers use Code Signing Certificates to digitally sign apps, drivers, executables, and software programs, allowing end users to ensure that the code they get has not been modified or corrupted by a third party.)
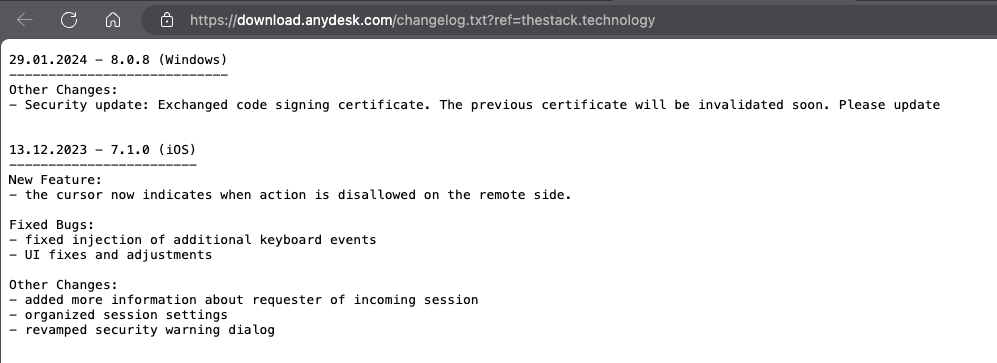
Fig. Changelog indicating invalidation of the previous code signing certificate
Previous versions of the software were found to be signed with the name ‘philandro Software GmbH’ with a serial number of 0dbf152deaf0b981a8a938d53f769db8. The current version is now signed by ‘AnyDesk Software GmbH,’ and the serial number is 0a8177fcd8936a91b5e0eddf995b0ba5.
AnyDesk did not say when or how its production systems were breached. It is unclear whether any information was stolen as a result of the incident. However, it highlighted that there is no evidence of any end-user systems being affected.
Detection:
The following query can be used to locate executables in an environment that were signed with the previous, to-be-revoked certificate (including prior versions of the Anydesk client):
DeviceFileCertificateInfo
| where TimeGenerated >= ago(31d)
| where CertificateSerialNumber == “0dbf152deaf0b981a8a938d53f769db8”
and Signer == “philandro Software GmbH”
| project TimeGenerated, DeviceName, CertificateSerialNumber, Signer
Recommendations:
It is strongly suggested that all users install the most recent version of the software (version 8.0.8 for Windows; other binaries continue to utilize the old certificate), as the old code signing certificate will be revoked soon. Anydesk has initiated a mandatory password reset for their customer portal, my.anydesk.com, and has advised users to update their passwords. Users are urged to also change any identical passwords used on other portals.