Cloud security platform Zscaler, which offers complete network security and visibility, is essential to the implementation of SASE solutions.
Background:
The emergence of cloud-based services has changed how businesses approach network security in the always changing field of cybersecurity. The increasing prevalence of Secure Access Service Edge (SASE) designs has placed security teams in charge of protecting distributed networks and users who can access resources at any time, from any location. Cloud security platform Zscaler, which offers complete network security and visibility, is essential to the implementation of SASE solutions.
Threat detection and response are essential elements of a successful cybersecurity strategy. Zscaler’s logging features provide a variety of useful information that may be used to improve threat detection and response plans in a SASE framework. Organizations may assure the integrity and confidentiality of their networks and data by identifying and mitigating security risks more successfully through the cognitive inspection of Zscaler logs.
Zscaler as a proxy server acts as a middleman between end users and the websites or services they visit online. It offers features such as web filtering, enhanced security, and data caching to boost network efficiency. Proxies also conceal user IP addresses, facilitating anonymous web browsing and aiding in internet usage management within organizations.
SOC Goals:
A broader definition of security operations is a function that recognizes, looks into, and eliminates threats. The following are security operations’ four primary purposes:
- Monitoring, classifying, and triaging events in real time
- Analysis, prioritizing, and threat assessment
- Remedial action, recovery, and incident response
- Compliance management, auditing, and vulnerability assessment
SOC Use Cases for Proxy Logs:
Proxy logs can serve various purposes in enhancing security and network management. Here are some potential use cases for leveraging proxy logs:
Malware Detection:
Objective: Identify and respond to malware downloads or connections to malicious domains.
Method: Monitor URLs, file types, and destinations against threat intelligence feeds. Generate alerts for traffic to high-risk categories or flagged domains.
Data Exfiltration:
Objective: Spot potential data leakage or exfiltration attempts.
Method: Watch for unusual data transfers to external sites, especially untrusted ones. Track sensitive file types being uploaded externally.
Phishing Detection:
Objective: Detect access to phishing sites.
Method: Utilize URL and domain reputation scores to flag requests to known phishing sites. Highlight instances of users submitting credentials to suspicious domains.
Anomaly Detection:
Objective: Identify abnormal web browsing behavior indicating compromised credentials or insider threats.
Method: Analyze patterns in web requests frequency, timing, and volume. Set alerts for unusual access times, high data transfer rates, or accesses from unusual locations.
Compliance Monitoring:
Objective: Ensure compliance with corporate web usage policies and regulations.
Method: Monitor and report on access to restricted categories during work hours. Implement real-time blocking or alerting for policy violations.
Bandwidth Management:
Objective: Optimize network bandwidth usage.
Method: Analyze traffic patterns to identify non-business related high bandwidth usage. Use this information to shape traffic and prioritize critical applications.
Secure Socket Layer (SSL) Inspection:
Objective: Detect unauthorized encrypted traffic.
Method: Monitor for abnormal increases in encrypted traffic or certificate errors, signaling potential MITM attacks or connections to compromised sites.
VPN and Remote Access Monitoring:
Objective: Monitor and secure VPN and remote access.
Method: Track all VPN access, identify geolocation anomalies, and ensure appropriate use of remote access privileges.
These use cases can enhance security posture, ensure regulatory compliance, and optimize network performance by leveraging insights from proxy logs.
Zscaler Logs:
Zscaler creates a number of logs that record specifics about user activity, security events, and network traffic. These logs reveal information about who, where, and how users are accessing different resources. Major log types consist of:
Web insight log:
Access to log data about web transactions and security events, including requested URLs, Page Risk Index scores for each, sent and received bytes, and more, is made possible via Web Insights and Logs.
Mobile insight log:
Access to log data about web transactions and security events, including requested URLs, Page Risk Index scores for each, sent and received bytes, and more, is made possible via Mobile Insights and Logs.
Firewall insight log:
Access to log data about network transactions, firewall policies that have been applied, client and server information, and network services and applications is made possible via firewall insights and logs.
DNS insight log:
Access to information like the DNS request and response details is possible with DNS Insights and Logs. You can specify the DNS traffic information you wish to view by using data kinds and filters.
SaaS security insight log:
Access to log data about online transactions and security events unique to defined SaaS apps and tenants is made possible by SaaS Security Insights and Logs.
Rich threat context and other helpful information for threat hunting and remediation are included in the verbose record known as NSS (Nanolog streaming service) for weblog stream, which comes in a compressed format. There are over a hundred fields in it. Selectively filtering and sending web proxy, tunnel, SaaS security logs, and warnings logs to your SIEM as distinct feeds is possible using NSS feeds.
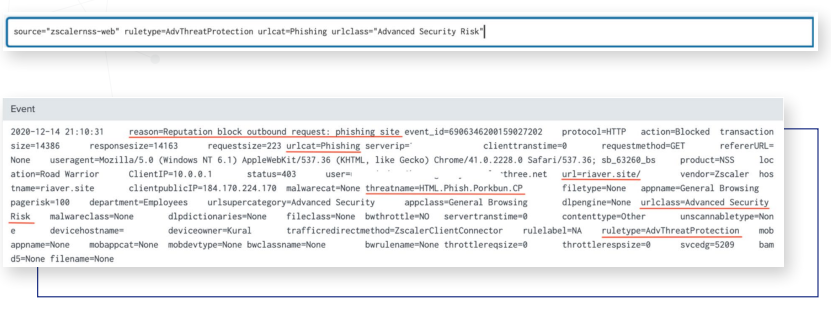
Detection of Malware/Phishing Traffic through the Logs:
Detecting Phishing Attempts:
The NSS weblog can be analyzed using the following search parameters and essential fields to spot phishing attempts:
ruleType=”AdvThreatProtection”, urlCat=”WebSpam”
ruleType=”AdvThreatProtection”, urlCat=”Phishing”, urlclass=”Advanced Security Risk”
Detecting Botnet/C2 Activity:
To filter the Insights log and find botnets or command-and-control activity, the following search parameters and important fields are helpful:
ruleType=”AdvThreatProtection”, urlCat=”Botnets”
ruleType=”AdvThreatProtection”, urlCat=”Botnets”, urlclass=”Advanced Security Risk”
reason=“IPS block outbound request: botnet command and control traffic”
reason=“Reputation block outbound request: botnet site”
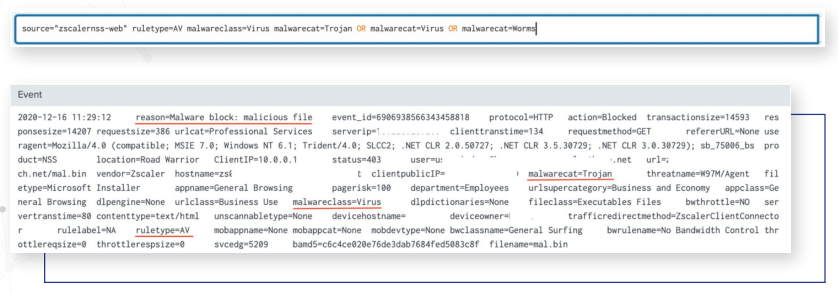
Detecting Malware Activity:
The NSS weblog can be examined using the following search parameters and key fields to find instances of malware, trojans, RATs, password stealers, and worm attempts:
ruleType=”AV” malwareclass=”Virus”
malwarecat=”Trojan.” “Macro Virus,” “Malware Tool,” “Password Stealer,” “Worms,” “Unrecognized Virus”
reason=”Malware block:malicious file”
urlclass=”Advanced Security Risk”
urlcat=”Malicious URLs”, “Suspected Spyware or Adware”
urlclass=”Advanced Security Risk”
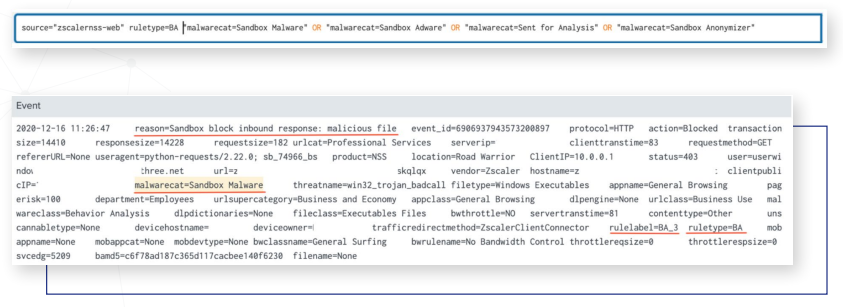
Detecting Unknown Malware:
When analyzing the NSS weblog to find files that were sent to the sandbox but are unknown, the following search parameters and key fields are helpful:
ruleType=”BA”
malwarecat=”Sent for Analysis,” “Sandbox Malware,” “Sandbox Adware,” Sandbox Anonymizer”
reason=”Allowed – No Active Content,’ “Quarantined,” “Sandbox block inbound response: malicious file,”
“Allowed and No Scan”
Remote Browser Isolation:
When a user accesses potentially harmful web content, remote browser isolation, also known as web isolation, establishes an isolated environment and presents the user with a cloud-hosted version of the content. RBI stops malware concealed in content from reaching the endpoint or spreading throughout a network by redirecting web browsing activity to a cloud domain without downloading the material. RBI enhances other crucial cybersecurity tasks by offering efficient defense against known and unknown threats in this manner.
The process of remote browser isolation is as follows:
- A user tries to access potentially malicious web content.
- The platform creates an isolated browser session based on the evaluation of the request against defined policies.
- The platform connects to the content and loads it onto the remote isolated browser.
- Rendered web content is streamed to the end user’s native browser as pixels over an HTML5 canvas from the platform.
Browser Isolation page